[TOC]
0x00 实践案例
1) 企业内部DNS主从服务搭建配置
实验目标: 内部DNS主从搭建以及DNS服务器安全配置;
环境准备:

[TOC]
实验目标: 内部DNS主从搭建以及DNS服务器安全配置;
环境准备:1
2
3
4
5
6
7
8# 主机
master - ns1 - 192.168.12.254 # 主DNS服务器
slave - ns2 - 192.168.10.254 # 备DSN服务器
slave - ns3 - 192.168.4.254 # 备DSN服务器
any # 客户机器1
# OS 环境
Ubuntu 20.04.1 LTS (GNU/Linux 5.4.0-67-generic x86_64)
实践流程:
1 | # (1) 防火墙设置(后面没有特殊注明的即为三台主机都要执行) |
1 | # (2) Master DNS Server 配置文件在master - ns1机器上执行如下命令 |
描述: 此处配置192.168.4.254 以及 192.168.10.254两台北机器上进行操作;
1 | # (1) 创建 slave 存放同步的 zone 文件 |
1 | # 1) 区域配置(主、备) |
Step 5.bind相关配置文件所属者与所属组分配
1 | sudo chown -R bind:bind /var/cache/bind/ /etc/bind/ |
Step 6.重启named服务以及查看服务的启动状态
1 | # 1) 启动主dns |
1 | # (1) 测试 weiyigeek.cn 与 weiyigeek.top 的 NS 记录 |
1 | # 1) 添加一条正向解析 |
1 | # 0) 采用名称服务器控件实用程序进行重载 |
1 | # (1) Named 服务信息日志查询 |
描述: 在前一章我们讲解DNS主从的基本配置以及访问限制,但是对于在企业中实际运行我们需要考虑到方方面面的问题,例如伪造MAC地址以及IP地址,此时它就可以通过区域传输获取内部域名的对应服务器地址,为了防止此种安全问题的发生我们可以采用 TSIG (Transaction SIGnatures) 进行事务签名加密zone同步信息或者采用 DNSSEC 扩展对DNS 信息的加密认证。
Q: 什么是TSIG (Transaction SIGnatures)?
答: TSIG(交易网格)是一种身份验证DNS消息的机制,最初在RFC 2845中指定
作用: 它允许使用共享的秘密加密地签名 DNS 消息。TSIG 可用于任何 DNS 事务,
Tips : TSIG 的应用场景说明
例如,当基于 IP 的访问控制不足或需要被覆盖时,将某些服务器功能(例如递归查询)的访问限制给授权客户端,或在对服务器完整性至关重要时确保消息的真实性
例如,动态 UPDATE 消息或从主服务器传输到次要服务器的区域传输。
Tips : 补充介绍AXFR与IXFR介绍
Step 1.TSIG 密钥生成关键是tsig-key : hmac-md5, hmac-sha1, hmac-sha224, hmac-sha256, hmac-sha384, and hmac-sha512. The default is hmac-sha256
1 | # Tips:任何有效的DNS名称字符串都可以用作密钥名。 |
Step 2.将下述服务器之间共享的密钥,内容添加到每个服务器的 named.conf 文件中;
1 | # Tips: 查看生成的签名安全文本信息 |
Step 3.指示服务器使用密钥和TSIG-Based访问控制(如allow-query, allow-transfer, and allow-update)
1 | # 1.密钥也可以在服务器指令中指定。 |
1 | # (0) 将 dns-sync-keygen.key 文件分别上传到两台Slave服务器之中; |
1 | # (3) 修改两台slave服务器named.conf.conf.options和dns-sync-keygen.key权限以及所属者修改 |
Tips : 如果此时 Slave 服务器 没有设置 TSIG 密钥到 named.conf 配置文件中, 则出现以下错误 client @0x7f6008000cd0 192.168.12.254#59492: request has invalid signature: TSIG dns-server-keygen: tsig verify failure (BADKEY)
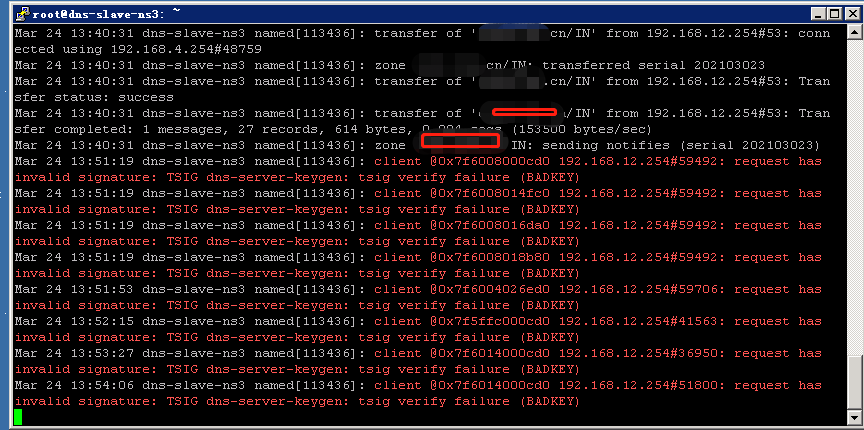
weiyigeek.top-Slave-Noconfig-TSIG
Tips : DNS客户端工具校验TSIG事物签名:
1 | # 1.使用命令 rndc tsig-list 列出服务器已知的TSIG密钥(主从)。 |
1 | C:\Users\WeiyiGeek>nslookup -qt=a sync.weiyigeek.top 192.168.4.254 |
Tips : 当任何服务器发送由 TSIG 签名的 DNS 请求时,它希望使用相同的密钥签署响应。如果未签署回复,或者签名无效,则拒绝回复。
Tips : 处理 TSIG 签名的消息可能会导致几个错误
描述: 应用程序实际上都是调用的操作系统的 DNS Resolver 进行域名解析的。在 Linux 中 DNS Resolver 由 glibc/musl 提供其配置文件为 /etc/resolv.conf。
Tips : 比如 Python 的 DNS 解析,就来自于标准库的 socket 包,这个包只是对底层 c 语言库的一个简单封装。
操作系统解析域名的三种方式:
hosts 文件
描述: 操作系统中还有一个特殊文件Linux 中的 /etc/hosts 和 Windows 中的 C:\Windows\System32\drivers\etc\hosts 存放着用户自定义的域名(或主机名)与IP地址对于关系。其优先级最高系统中的 DNS resolver 会首先查看这个 hosts 文件中有没有该域名的记录,如果有就直接返回了。没找到才会去查找本地 DNS 缓存、别的 DNS 服务器。
Tips : 只有部分专门用于网络诊断的应用程序(e.g. dig)不会依赖 OS 的 DNS 解析器,因此这个 hosts 会失效。hosts 对于绝大部分程序都有效。
Tips : 移动设备上 hosts 可能会失效,部分 app 会绕过系统,使用新兴的 HTTPDNS 协议进行 DNS 解析。
HTTPDNS
描述: 由于传统的 DNS 协议因为使用了明文的 UDP 协议,很容易被劫持。顺应移动互联网的兴起,目前一种新型的 DNS 协议——HTTPDNS 应用越来越广泛,国内的阿里云腾讯云都提供了这项功能。
Tips : HTTPDNS 通过 HTTP 协议直接向权威 DNS 服务器发起请求,绕过了一堆中间的 DNS 递归解析器。
Tips : HTTPDNS 协议需要程序自己引入 SDK,或者直接请求 HTTP API。
使用HTTPDNS的好处:
默认 DNS 服务器
描述: 操作系统的 DNS 解析器通常会允许我们配置1-3个上游 NameServers,DNS 查询会按配置中的顺序选用 DNS 服务器。
比如 Linux 就是通过 /etc/resolv.conf 配置 DNS 服务器的。1
2
3
4$ cat /etc/resolv.conf
nameserver 8.8.8.8
nameserver 8.8.4.4
search lan # DNS 搜索域
Q: 什么是DNS搜索域?
答: 讲到 DNS 搜索域需要复习一哈全限定域名(Full Qulified Domain Name, FQDN),即一个域名的完整名称,
www.baidu.com
www.baidu.com.: 末尾的 . 表示根域,说明 www.baidu.com 是一个 FQDN,因此不会使用搜索域!www.baidu.com: 末尾没 .,但是域名包含不止一个 .。首先当作 FQDN 进行查询没查找再按顺序在各搜索域中查询。.的临界个数,默认是 1.就如上面说例举的,在没有 DNS 搜索域 这个东西的条件下,我们访问任何域名,都必须输入一个全限定域名 FQDN。
有了搜索域我们就可以稍微偷点懒,省略掉域名的一部分后缀,让 DNS Resolver 自己去在各搜索域中搜索。1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55# 0) 获取k8s的kube-dns
~$ kubectl get svc -n kube-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kube-dns ClusterIP 10.96.0.10 <none> 53/UDP,53/TCP,9153/TCP 68d
# 1) 例如 我们设置 /etc/resolv.conf 如下
# nameserver 192.168.12.254
# search weiyigeek.top weiyigeek.cn
nameserver 10.96.0.10
search default.svc.cluster.local svc.cluster.local cluster.local
# ndots:5 是指少于 5 个 dots 的域名,都首先当作非 FQDN 看待优先在搜索域里面查找;
options ndots:5
# 2) 输入一个不存在的域名查看尝试过程
~$ host -v weiyigeek
# Trying "weiyigeek.default.svc.cluster.local"
# Trying "weiyigeek.svc.cluster.local"
# Trying "weiyigeek.cluster.local"
# Trying "weiyigeek"
# Host weiyigeek not found: 3(NXDOMAIN)
# Received 102 bytes from 10.96.0.10#53 in 47 ms
# 3) 输入一个集群中存在域名它将会在搜索域中进行解析请求(A / AAAA / MX)记录
~$ kubectl get svc
# NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
# weiyigeek NodePort 10.107.122.223 <none> 8080:30089/TCP 15d
~$ host -d -v weiyigeek
Trying "weiyigeek.default.svc.cluster.local" # 描述:一来就找到该FQDN解析的IP地址
# ;; ->>HEADE opcode: QUERY, status: NOERROR, id: 7138
# ;; flags: qr aa rd; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0
# ;; QUESTION SECTION: # 询问
# ;weiyigeek.default.svc.cluster.local. IN A # A 记录
# ;; ANSWER SECTION: # 回答
# weiyigeek.default.svc.cluster.local. 30 IN A 10.107.122.223
# Received 118 bytes from 10.96.0.10#53 in 3 ms
Trying "weiyigeek.default.svc.cluster.local"
# ;; ->>HEADER opcode: QUERY, status: NOERROR, id: 32192
# ;; flags: qr aa rd; QUERY: 1, ANSWER: 0, AUTHORITY: 1, ADDITIONAL: 0
# ;; QUESTION SECTION:
# ;weiyigeek.default.svc.cluster.local. IN AAAA # AAAA 记录
# ;; AUTHORITY SECTION:
# cluster.local. 30 IN SOA ns.dns.cluster.local. hostmaster.cluster.local. 1616058438 7200 1800 86400 30
# Received 153 bytes from 10.96.0.10#53 in 0 ms
Trying "weiyigeek.default.svc.cluster.local"
# ;; ->>HEADER opcode: QUERY, status: NOERROR, id: 11848
# ;; flags: qr aa rd; QUERY: 1, ANSWER: 0, AUTHORITY: 1, ADDITIONAL: 0
# ;; QUESTION SECTION:
# ;weiyigeek.default.svc.cluster.local. IN MX # MX 记录
# ;; AUTHORITY SECTION:
# cluster.local. 30 IN SOA ns.dns.cluster.local. hostmaster.cluster.local. 1616058426 7200 1800 86400 30
# Received 153 bytes from 10.96.0.10#53 in 0 ms
Tips : 在靠前的 DNS 服务器没有响应(timeout)时,才会使用后续的 DNS 服务器!所以指定的服务器中的 DNS 记录最好完全一致!!!不要把第一个配内网 DNS,第二个配外网!!!
Q: 什么是dns缓存?
答: 每当我们尝试访问带有网站时都会执行DNS名称解析查询来解析其IP地址。 操作系统缓存此数据,以避免每次都与名称服务器联系。
Q: 为什么要清除DNS缓存? (Why to Clear DNS Cache?)
答: 常常会出现以下场景例如网站的IP地址在移至另一台服务器时会更改或者管理员更改了DNS解析记录(
受生存时间(TTL)管控)。在这种情况下如果我们点击了缓存的IP地址,则该网站将无法正常运行。
DNS条目具有与之关联的”生存时间(TTL)”值,该值告诉操作系统名称解析服务何时使DNS缓存无效。
如果您想在TTL过期之前联系到新的IP地址,则唯一的解决方案是刷新DNS缓存。
Q: 如何在Ubuntu/Windows上清除DNS缓存?1
2
3
4
5
6
7
8# Ubuntu
# Tips: --flush-caches 选项仅仅只是清除DNS缓存
sudo systemd-resolve --flush-caches
# Tips: 重新启动systemd解析的服务可以清除所有DNS缓存统计信息
# sudo systemctl restart systemd-resolved
# Windows
ipconfig /flushdns
描述: 在windows或者Linux常用的DNS服务器解析测试采用以下软件进行;
描述: 支持多平台、应用广泛, 其优点使用简单、异动;1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30# (1) 使用示例 -t type
# This option specifies the query type. The type argument can be any recognized query type: CNAME, NS, SOA, TXT, DNSKEY, AXFR, etc.
nslookup -qt=SOA/A/CNAME/MX/NS/TXT www.weiyigeek.top # -qt type指定DNS解析类型
C:\Users\WeiyiGeek>nslookup -qt=a weiyigeek.top 192.168.12.254
服务器: ns1.weiyigeek.top
Address: 192.168.12.254
非权威应答:
名称: weiyigeek.top
Addresses: 172.67.189.218
104.21.10.9
# (2) 交互式
nslookup
> server 172.16.102.14
> set q=a //设置DNS解析类型
> www.weiyigeek.top
> set q=ns
> www.weiyigeek.top
服务器: UnKnown
Address: 192.168.2.1
weiyigeek.top
primary name server = ns3.dnsv3.com
responsible mail addr = enterprise1dnsadmin.dnspod.com
serial = 1500274720
refresh = 3600 (1 hour)
retry = 180 (3 mins)
expire = 1209600 (14 days)
default TTL = 180 (3 mins)
Linux 平台1
2# 1.A记录查询
$ nslookup -query=A service-headless.default.svc.cluster.local.
描述: 主要运行在Linux平台上, 其优点比较专业;1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92# (1) 默认查询A记录
dig www.baidu.com @172.16.102.14
# ; <<>> DiG 9.16.1-Ubuntu <<>> www.baidu.com @192.168.4.254
# ;; Got answer:
# ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 20227
# ;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 0, ADDITIONAL: 1
# ;; OPT PSEUDOSECTION:
# ; EDNS: version: 0, flags:; udp: 4096
# ; COOKIE: fdbde72c243a04c60100000060587950b128dc5a23826a27 (good)
# ;; QUESTION SECTION:
# ;www.baidu.com. IN A
# ;; ANSWER SECTION:
# www.baidu.com. 99 IN CNAME www.a.shifen.com.
# www.a.shifen.com. 98 IN A 14.215.177.39
# www.a.shifen.com. 98 IN A 14.215.177.38
# ;; Query time: 19 msec
# ;; SERVER: 192.168.4.254#53(192.168.4.254)
# ;; WHEN: Mon Mar 22 19:02:40 CST 2021
# ;; MSG SIZE rcvd: 132
# (2) -t NS解析类型
dig -t ns www.baidu.com
# (3) -x ip反查域名
dig -x 192.168.12.13 @192.168.12.254
# ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 56847
# ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
# ;; OPT PSEUDOSECTION:
# ; EDNS: version: 0, flags:; udp: 4096
# ; COOKIE: a78353f6f0787a7d010000006058799c1af1ea827274eb9f (good)
# ;; QUESTION SECTION:
# ;13.12.168.192.in-addr.arpa. IN PTR
# ;; ANSWER SECTION:
# 13.12.168.192.in-addr.arpa. 86400 IN PTR s.weiyigeek.top.
# (4) 复现正向查询的流程
dig +trace baidu.com
# 先在根域中查找
. 503232 IN NS g.root-servers.net.
....
. 503232 IN NS i.root-servers.net.
. 518317 IN RRSIG NS 8 0 518400 20210403170000 20210321160000 42351 . ... XoGqZA==
;; Received 1137 bytes from 192.168.12.254#53(192.168.12.254) in 0 ms
# 其次在顶级域
com. 172800 IN NS a.gtld-servers.net.
....
com. 172800 IN NS l.gtld-servers.net.
com. 86400 IN DS 30909 8 2 E2D3C916F6DEEAC73294E8268FB5885044A833FC5459588F4A9184CF C41A5766
com. 86400 IN RRSIG DS 8 1 86400 20210403170000 20210321160000 42351 ....
;; Received 1169 bytes from 199.7.83.42#53(l.root-servers.net) in 27 ms
# 在次级域ns获得百度的A记录
baidu.com. 172800 IN NS ns2.baidu.com.
baidu.com. 172800 IN NS ns3.baidu.com.
baidu.com. 172800 IN NS ns4.baidu.com.
baidu.com. 172800 IN NS ns1.baidu.com.
baidu.com. 172800 IN NS ns7.baidu.com.
CK0POJMG874LJREF7EFN8430QVIT8BSM.com. 86400 IN NSEC3 1 1 0 - CK0Q1GIN43N1ARRC9OSM6QPQR81H5M9A NS SOA RRSIG DNSKEY NSEC3PARAM
CK0POJMG874LJREF7EFN8430QVIT8BSM.com. 86400 IN RRSIG NSEC3 8 2 86400 20210329044039 20210322033039 58540 com.
HPVUSBDNI26UDNIV6R0SV14GC3KGR4JP.com. 86400 IN NSEC3 1 1 0 - HPVVN3Q5E5GOQP2QFE2LEM4SVB9C0SJ6 NS DS RRSIG
HPVUSBDNI26UDNIV6R0SV14GC3KGR4JP.com. 86400 IN RRSIG NSEC3 8 2 86400 20210329061254 20210322050254 58540
;; Received 757 bytes from 192.54.112.30#53(h.gtld-servers.net) in 215 ms
# 获得A记录
baidu.com. 600 IN A 220.181.38.148
baidu.com. 600 IN A 39.156.69.79
baidu.com. 86400 IN NS ns7.baidu.com.
baidu.com. 86400 IN NS ns2.baidu.com.
baidu.com. 86400 IN NS ns4.baidu.com.
baidu.com. 86400 IN NS ns3.baidu.com.
baidu.com. 86400 IN NS dns.baidu.com.
;; Received 240 bytes from 14.215.178.80#53(ns4.baidu.com) in 35 ms
# (5) 复现反向查询的流程(此处以百度邮箱为例)
ping mx21.baidu.com # 获得地址
~$ dig -x 220.181.3.85 @192.168.4.254
~$ dig -t ptr 85.3.181.220.in-addr.arpa. @192.168.4.254
# ;; QUESTION SECTION:
# ;85.3.181.220.in-addr.arpa. IN PTR
# ;; ANSWER SECTION:
# 85.3.181.220.in-addr.arpa. 3600 IN PTR mx21.baidu.com.
# (6) 直接输出一个域名解析地址
dig +short blog.weiyigeek.top
# 172.67.189.218
dig +short www.weiyigeek.top
for i in $(dig +short www.weiyigeek.top);do echo IP:${i};done
# IP:104.21.10.9
# IP:172.67.189.218
描述: 使用较多, 简单、明了,它基本就是 dig 的弱化版;1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52# (1) -t type指定DNS解析类型
host -t SOA www.weiyigeek.top
host -t NS www.weiyigeek.top
host -t CNAME www.weiyigeek.top
host -t A www.weiyigeek.top
host -t MX www.weiyigeek.top
host -t TXT www.weiyigeek.top
# (2) 不过 host 有个有点就是能打印出它测试过的所有 FQDN (此处也能体现搜索域)
host -a weiyigeek.cn
# Trying "weiyigeek.cn"
# ;; - opcode: QUERY, status: NOERROR, id: 25817
# ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 5, AUTHORITY: 0, ADDITIONAL: 3
# ;; QUESTION SECTION:
# ;weiyigeek.cn. IN ANY
# ;; ANSWER SECTION:
# weiyigeek.cn. 86400 IN SOA ns1.weiyigeek.cn. admin.weiyigeek.cn. 3 50400 86400 604800 86400
# weiyigeek.cn. 86400 IN NS ns1.weiyigeek.cn.
# weiyigeek.cn. 86400 IN NS ns2.weiyigeek.cn.
# weiyigeek.cn. 86400 IN NS ns3.weiyigeek.cn.
# weiyigeek.cn. 86400 IN A 192.168.10.47
# ;; ADDITIONAL SECTION:
# ns1.weiyigeek.cn. 86400 IN A 192.168.12.254
# ns2.weiyigeek.cn. 86400 IN A 192.168.10.254
# ns3.weiyigeek.cn. 86400 IN A 192.168.4.254
# (3) -v 请求详细流程 (设置搜索域时可以看到 A/AAAA/MX 请求)
~$ host -v oa
Trying "oa.weiyigeek.top"
Trying "oa.weiyigeek.cn"
# ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 64579
# ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0
# .....
# ;; QUESTION SECTION:
# ;oa.weiyigeek.cn. IN A
# ;; ANSWER SECTION:
# oa.weiyigeek.cn. 604800 IN A 192.168.100.96
# .....
# ;; QUESTION SECTION:
# ;oa.weiyigeek.cn. IN AAAA
# ;; AUTHORITY SECTION:
# weiyigeek.cn. 604800 IN SOA ns1.weiyigeek.cn. admin.weiyigeek.cn. 3 600 86400 2419200 604800
# .....
# ;; QUESTION SECTION:
# ;oa.weiyigeek.cn. IN MX
# ;; AUTHORITY SECTION:
# weiyigeek.cn. 604800 IN SOA ns1.weiyigeek.cn. admin.weiyigeek.cn. 3 600 86400 2419200 604800
# Received 75 bytes from 192.168.12.254#53 in 0 ms
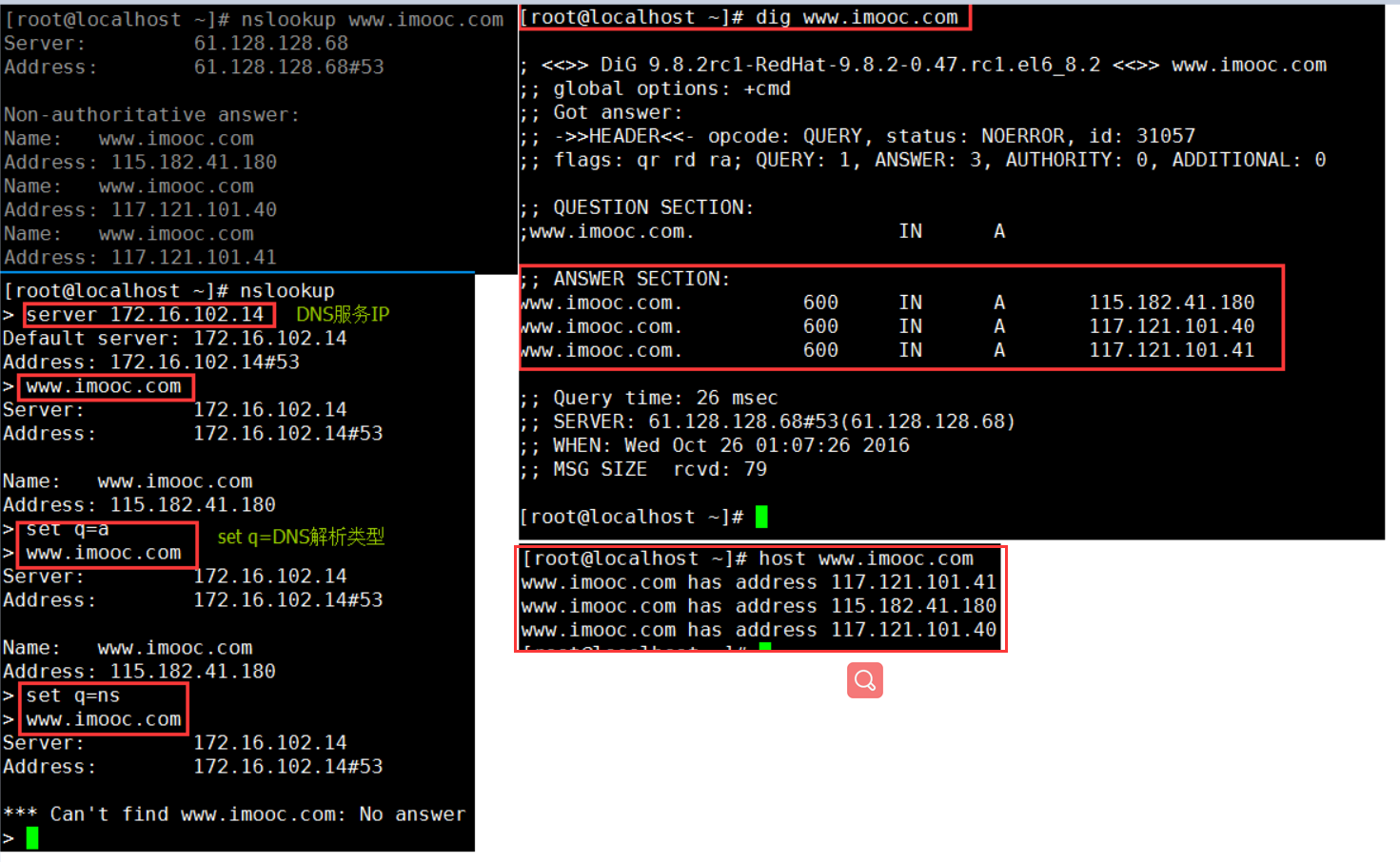
weiyigeek.top-DNS正向解析客户端工具
描述: whois目录服务的客户端1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30# SYNOPSIS
whois [ { -h | --host } HOST ] [ { -p | --port } PORT ] [ -abBcdGHIKlLmMrRx ] [ -g SOURCE:FIRST-LAST ] [ -i ATTR[,ATTR]... ] [ -s SOURCE[,SOURCE]... ] [ -T TYPE[,TYPE]... ] [ --verbose ] OBJECT
whois -q KEYWORD
whois -t TYPE
whois -v TYPE
# 参数:
-h HOST, --host=HOST # Connect to HOST.
-p PORT, --port=PORT # Connect to PORT.
-H # Do not display the legal disclaimers that some registries like to show you.
-I # First query whois.iana.org and then follow its referral to the whois server authoritative for that request. This works for IP addresses, AS numbers and domains. BEWARE: this implies that the IANA server will re‐ceive your complete query.
--verbose Be verbose.
Other options are flags understood by whois.ripe.net and some other RIPE-like servers:
-a Also search all the mirrored databases.
-b Return brief IP address ranges with abuse contact.
-B Disable objects filtering. (Show the e-mail addresses.)
-c Return the smallest IP address range with a reference to an irt object.
-d Return the reverse DNS delegation object too.
-g SOURCE:FIRST-LAST # Search updates from SOURCE database between FIRST and LAST update serial number. It is useful to obtain Near Real Time Mirroring stream.
-G #Disable grouping of associated objects.
-i ATTR[,ATTR]... # Inverse-search objects having associated attributes. ATTR is the attribute name, while the positional OBJECT argument is the attribute value.
-K Return primary key attributes only. An exception is the members attribute of set objects, which is always returned. Another exception are all attributes of the objects organisation, person and role, that are never returned.
-l Return the one level less specific object.
-L Return all levels of less specific objects.
-m Return all one level more specific objects.
-M Return all levels of more specific objects.
--help Display online help.
--version Display the program version.
基础实例:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26# 1) 域名提供商信息查询(现在基本都是)
~$ whois weiyigeek.top
Domain Name: weiyigeek.top
Registry Domain ID: D20200225G10001G_34088337-top
Registrar WHOIS Server: whois.dnspod.cn
Registrar URL: https://www.dnspod.cn
Updated Date: 2020-04-25T06:49:26Z
Creation Date: 2020-02-25T03:50:39Z
Registry Expiry Date: 2030-02-25T03:50:39Z
Registrar: DNSPod, Inc.
Registrar IANA ID: 1697
Registrar Abuse Contact Email: abuse@dnspod.com
Registrar Abuse Contact Phone: +86.95716
Domain Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited
Registry Registrant ID: REDACTED FOR PRIVACY
Registrant Name: REDACTED FOR PRIVACY
Registrant Organization: weiyigeek
Registrant Street: REDACTED FOR PRIVACY
Registrant City: REDACTED FOR PRIVACY
Registrant State/Province: chong qing shi
Registrant Postal Code: REDACTED FOR PRIVACY
Registrant Country: CN
Registrant Phone: REDACTED FOR PRIVACY
Registrant Phone Ext: REDACTED FOR PRIVACY
Registrant Fax: REDACTED FOR PRIVACY
Registrant Fax Ext: REDACTED FOR PRIVACY
Tips : dig 工具未来可能会被 drill 取代。
Named 配置测试:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23tee /tmp/dns-test.sh <<'END'
#!/bin/bash
# 1) 区域配置(主、备)
if [ $# -eq 0 ];then
echo "Usage: $0 /var/cache/bind"
zonedir="/var/cache/bind"
else
zonedir=$1 # /var/cache/bind/master
fi
named-checkconf -p
# 2) 内部解析zone配置
for zone in $(ls ${zonedir});do
echo "# ${zone} ---------------------------"
named-checkzone ${zone} ${zonedir}/${zone}
echo -e "\n"
done
END
chmod +x /tmp/dns-test.sh
bash /tmp/dns-test.sh /var/cache/bind/master
问题描述: 之前一直用的windows版本的bind9服务器。配置文件稍微改动一下路径直接拿来用。可以运行但是总是提示错误validating com/DS: no valid signature found。
描述: 通过参考官网的说明发现可以由于时区或者dnssec密钥不正确以及不存在导致导致no valid signature found错误。
解决办法: 修改bind9的options配置如下即可使用,如果要使用dnssec需要生成Generating Keys(帮助地址)。1
2
3//dnssec-enable yes;
dnssec-validation no;
//dnssec-lookaside auto;
错误信息:1
2
3
4Mar 22 14:54:32 dns-server named[70775]: client @0x7f418c000cd0 10.20.172.106#54935 (edge.microsoft.com): query (cache) 'edge.microsoft.com/A/IN' denied
Mar 22 14:54:32 dns-server named[70775]: client @0x7f418c000cd0 10.20.172.106#54935 (edge.microsoft.com): query failed (REFUSED) for edge.microsoft.com/IN/A at query.c:5425
Mar 22 14:55:09 dns-server named[70775]: client @0x7f4174013dd0 10.20.172.106#59712 (edge.activity.windows.com): query (cache) 'edge.activity.windows.com/A/IN' denied
Mar 22 14:55:09 dns-server named[70775]: client @0x7f4174013dd0 10.20.172.106#59712 (edge.activity.windows.com): query failed (REFUSED) for edge.activity.windows.com/IN/A at query.c:5425
错误原因: 从字面意思来看就是Client查询无权限
解决办法: 在named.conf中添加allow-query { any; };配置。
你好看友,欢迎关注博主微信公众号哟! ❤
这将是我持续更新文章的动力源泉,谢谢支持!(๑′ᴗ‵๑)
温馨提示: 未解锁的用户不能粘贴复制文章内容哟!
方式1.请访问本博主的B站【WeiyiGeek】首页关注UP主,
将自动随机获取解锁验证码。
Method 2.Please visit 【My Twitter】. There is an article verification code in the homepage.
方式3.扫一扫下方二维码,关注本站官方公众号
回复:验证码
将获取解锁(有效期7天)本站所有技术文章哟!

@WeiyiGeek - 为了能到远方,脚下的每一步都不能少
欢迎各位志同道合的朋友一起学习交流,如文章有误请在下方留下您宝贵的经验知识,个人邮箱地址【master#weiyigeek.top】或者个人公众号【WeiyiGeek】联系我。
更多文章来源于【WeiyiGeek Blog - 为了能到远方,脚下的每一步都不能少】, 个人首页地址( https://weiyigeek.top )
专栏书写不易,如果您觉得这个专栏还不错的,请给这篇专栏 【点个赞、投个币、收个藏、关个注、转个发、赞个助】,这将对我的肯定,我将持续整理发布更多优质原创文章!。
最后更新时间:
文章原始路径:_posts/系统运维/Application/DNS/DNS主从服务之企业内部搭建与安全配置实践.md
转载注明出处,原文地址:https://blog.weiyigeek.top/2020/1-20-541.html
本站文章内容遵循 知识共享 署名 - 非商业性 - 相同方式共享 4.0 国际协议