[TOC]
快速入门 描述:组策略是建立Windows安全环境的重要手段,尤其是在Windows域环境下;gpedit.msc在窗口界面下访问组策略,然而我们有木有办法可以再命令行下进行设置,答案肯定是有的就是今天的主人公 secedit.exe;
weiyigeek.top-gpedit.msc
组策略的计算机安全策略模板存放路径
%SYSTEMROOT%\security\templates
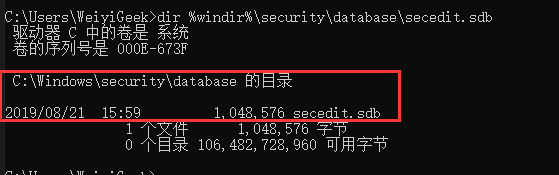
系统默认的安全数据库路径
%windir%\security\database\secedit.sdb
如果没有/log指定配置操作信息将被记录到scesrv.log
%windir%\security\logs目录之中
weiyigeek.top-secedit.sdb
基础语法:
[TOC]
快速入门 描述:组策略是建立Windows安全环境的重要手段,尤其是在Windows域环境下;gpedit.msc在窗口界面下访问组策略,然而我们有木有办法可以再命令行下进行设置,答案肯定是有的就是今天的主人公 secedit.exe;
weiyigeek.top-gpedit.msc
组策略的计算机安全策略模板存放路径
%SYSTEMROOT%\security\templates
系统默认的安全数据库路径
%windir%\security\database\secedit.sdb
如果没有/log指定配置操作信息将被记录到scesrv.log
%windir%\security\logs目录之中
weiyigeek.top-secedit.sdb
基础语法:1 2 3 4 5 此命令的语法为: secedit [/configure | /analyze | /import | /export | /validate | /generaterollback] 参数: /quit 安静模式
secedit 命令详述 secedit /export 描述:允许你导出保存在数据库中的安全设置。1 2 3 4 5 6 7 8 9 10 11 12 13 14 语法: secedit /export [/db filename] [/mergedpolicy] /cfg filename [/areas area1 area2...] [/log filename] 参数: /db filename - 指定要导出数据的数据库。如果没有指定,将使用系统安全数据库。 /cfg filename - 指定要导出数据库内容的安全模板。 /mergedpolicy - 合并并且导出域和本地策略安全设置。 /areas - 指定要应用到系统的安全性范围。如果没有指定此参数,在数据库中定义的所有安全性设置都将应用到系统中。 要配置多个范围,用空格将它们分开。下列安全性范围是受支持的: * SECURITYPOLICY - 包括帐户策略,审核策略,事件日志设置和安全选项。 * GROUP_MGMT - 包括受限制的组设置 * USER_RIGHTS - 包括用户权限分配 * REGKEYS - 包括注册表权限 * FILESTORE - 包括文件系统权限 * SERVICES - 包括系统服务设置 /log filename - 指定要记录导出操作状态的文件。
基础信息:1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 secedit /export /cfg current.inf /log secedit.log $type current.inf [Unicode] Unicode =yes [System Access] MinimumPasswordAge = 0 MaximumPasswordAge = 42 MinimumPasswordLength = 0 PasswordComplexity = 0 ;是否启用密码复杂度PasswordHistorySize = 0 LockoutBadCount = 0 ;锁定次数RequireLogonToChangePassword = 0 ;登录就需要登录密码ForceLogoffWhenHourExpire = 0 ;强制下线NewAdministratorName = "Administrator" ;管理员的默认名称NewGuestName = "Guest" ClearTextPassword = 0 LSAAnonymousNameLookup = 0 EnableAdminAccount = 0 ;是否启用管理员账户EnableGuestAccount = 0 [Event Audit] AuditSystemEvents =3 ;审核系统事件 成功、失败AuditLogonEvents = 3 AuditObjectAccess = 3 AuditPrivilegeUse = 2 AuditPolicyChange = 3 AuditAccountManage = 3 AuditProcessTracking = 2 ;审核过程追踪 失败AuditDSAccess = 1 ;审核目录服务访问 成功AuditAccountLogon = 3 [Registry Values] MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Setup\RecoveryConsole\SecurityLevel=4,0 MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Setup\RecoveryConsole\SetCommand=4,0 MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\CachedLogonsCount=1,"10" MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\ForceUnlockLogon=4,0 MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\PasswordExpiryWarning=4,5 MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\ScRemoveOption=1,"0" MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\ConsentPromptBehaviorAdmin=4,5 MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\ConsentPromptBehaviorUser=4,3 MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\DontDisplayLastUserName=4,0 MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\EnableInstallerDetection=4,1 MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\EnableLUA=4,1 MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\EnableSecureUIAPaths=4,1 MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\EnableUIADesktopToggle=4,0 MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\EnableVirtualization=4,1 MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\LegalNoticeCaption=1,"" MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\LegalNoticeText=7, MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\PromptOnSecureDesktop=4,1 MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\ScForceOption=4,0 MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\ShutdownWithoutLogon=4,1 MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\UndockWithoutLogon=4,1 MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\ValidateAdminCodeSignatures=4,0 MACHINE\Software\Policies\Microsoft\Windows\Safer\CodeIdentifiers\AuthenticodeEnabled=4,0 MACHINE\System\CurrentControlSet\Control\Lsa\AuditBaseObjects=4,0 MACHINE\System\CurrentControlSet\Control\Lsa\CrashOnAuditFail=4,0 MACHINE\System\CurrentControlSet\Control\Lsa\DisableDomainCreds=4,0 MACHINE\System\CurrentControlSet\Control\Lsa\EveryoneIncludesAnonymous=4,0 MACHINE\System\CurrentControlSet\Control\Lsa\FIPSAlgorithmPolicy\Enabled=4,0 MACHINE\System\CurrentControlSet\Control\Lsa\ForceGuest=4,0 MACHINE\System\CurrentControlSet\Control\Lsa\FullPrivilegeAuditing=3,0 MACHINE\System\CurrentControlSet\Control\Lsa\LimitBlankPasswordUse=4,1 MACHINE\System\CurrentControlSet\Control\Lsa\MSV1_0\NTLMMinClientSec=4,536870912 MACHINE\System\CurrentControlSet\Control\Lsa\MSV1_0\NTLMMinServerSec=4,536870912 MACHINE\System\CurrentControlSet\Control\Lsa\NoLMHash=4,1 MACHINE\System\CurrentControlSet\Control\Lsa\RestrictAnonymous=4,0 MACHINE\System\CurrentControlSet\Control\Lsa\RestrictAnonymousSAM=4,1 MACHINE\System\CurrentControlSet\Control\Print\Providers\LanMan Print Services\Servers\AddPrinterDrivers=4,0 MACHINE\System\CurrentControlSet\Control\SecurePipeServers\Winreg\AllowedExactPaths\Machine=7,System\CurrentControlSet\Control\ProductOptions,System\CurrentControlSet\Control\Server Applications,Software\Microsoft\Windows NT\CurrentVersion MACHINE\System\CurrentControlSet\Control\SecurePipeServers\Winreg\AllowedPaths\Machine=7,System\CurrentControlSet\Control\Print\Printers,System\CurrentControlSet\Services\Eventlog,Software\Microsoft\OLAP Server,Software\Microsoft\Windows NT\CurrentVersion\Print,Software\Microsoft\Windows NT\CurrentVersion\Windows,System\CurrentControlSet\Control\ContentIndex,System\CurrentControlSet\Control\Terminal Server,System\CurrentControlSet\Control\Terminal Server\UserConfig,System\CurrentControlSet\Control\Terminal Server\DefaultUserConfiguration,Software\Microsoft\Windows NT\CurrentVersion\Perflib,System\CurrentControlSet\Services\SysmonLog MACHINE\System\CurrentControlSet\Control\Session Manager\Kernel\ObCaseInsensitive=4,1 MACHINE\System\CurrentControlSet\Control\Session Manager\Memory Management\ClearPageFileAtShutdown=4,0 MACHINE\System\CurrentControlSet\Control\Session Manager\ProtectionMode=4,1 MACHINE\System\CurrentControlSet\Control\Session Manager\SubSystems\optional=7, MACHINE\System\CurrentControlSet\Services\LanManServer\Parameters\AutoDisconnect=4,15 MACHINE\System\CurrentControlSet\Services\LanManServer\Parameters\EnableForcedLogOff=4,1 MACHINE\System\CurrentControlSet\Services\LanManServer\Parameters\EnableSecuritySignature=4,0 MACHINE\System\CurrentControlSet\Services\LanManServer\Parameters\NullSessionPipes=7, MACHINE\System\CurrentControlSet\Services\LanManServer\Parameters\RequireSecuritySignature=4,0 MACHINE\System\CurrentControlSet\Services\LanManServer\Parameters\RestrictNullSessAccess=4,1 MACHINE\System\CurrentControlSet\Services\LanmanWorkstation\Parameters\EnablePlainTextPassword=4,0 MACHINE\System\CurrentControlSet\Services\LanmanWorkstation\Parameters\EnableSecuritySignature=4,1 MACHINE\System\CurrentControlSet\Services\LanmanWorkstation\Parameters\RequireSecuritySignature=4,0 MACHINE\System\CurrentControlSet\Services\LDAP\LDAPClientIntegrity=4,1 MACHINE\System\CurrentControlSet\Services\Netlogon\Parameters\DisablePasswordChange=4,0 MACHINE\System\CurrentControlSet\Services\Netlogon\Parameters\MaximumPasswordAge=4,30 MACHINE\System\CurrentControlSet\Services\Netlogon\Parameters\RequireSignOrSeal=4,1 MACHINE\System\CurrentControlSet\Services\Netlogon\Parameters\RequireStrongKey=4,1 MACHINE\System\CurrentControlSet\Services\Netlogon\Parameters\SealSecureChannel=4,1 MACHINE\System\CurrentControlSet\Services\Netlogon\Parameters\SignSecureChannel=4,1 [Privilege Rights] SeNetworkLogonRight = *S-1 -1 -0 ,*S-1 -5 -32 -544 ,*S-1 -5 -32 -545 ,*S-1 -5 -32 -551 SeBackupPrivilege = *S-1 -5 -32 -544 ,*S-1 -5 -32 -551 SeChangeNotifyPrivilege = *S-1 -1 -0 ,*S-1 -5 -19 ,*S-1 -5 -20 ,*S-1 -5 -32 -544 ,*S-1 -5 -32 -545 ,*S-1 -5 -32 -551 SeSystemtimePrivilege = *S-1 -5 -19 ,*S-1 -5 -32 -544 SeCreatePagefilePrivilege = *S-1 -5 -32 -544 SeDebugPrivilege = *S-1 -5 -32 -544 SeRemoteShutdownPrivilege = *S-1 -5 -32 -544 SeAuditPrivilege = *S-1 -5 -19 ,*S-1 -5 -20 SeIncreaseQuotaPrivilege = *S-1 -5 -19 ,*S-1 -5 -20 ,*S-1 -5 -32 -544 SeIncreaseBasePriorityPrivilege = *S-1 -5 -32 -544 ,*S-1 -5 -90 -0 SeLoadDriverPrivilege = *S-1 -5 -32 -544 SeBatchLogonRight = *S-1 -5 -32 -544 ,*S-1 -5 -32 -551 ,*S-1 -5 -32 -559 SeServiceLogonRight = *S-1 -5 -80 -0 SeInteractiveLogonRight = __vmware__,Guest,*S-1 -5 -32 -544 ,*S-1 -5 -32 -545 ,*S-1 -5 -32 -551 SeSecurityPrivilege = *S-1 -5 -32 -544 SeSystemEnvironmentPrivilege = *S-1 -5 -32 -544 SeProfileSingleProcessPrivilege = *S-1 -5 -32 -544 SeSystemProfilePrivilege = *S-1 -5 -32 -544 ,*S-1 -5 -80 -3139157870 -2983391045 -3678747466 -658725712 -1809340420 SeAssignPrimaryTokenPrivilege = *S-1 -5 -19 ,*S-1 -5 -20 SeRestorePrivilege = *S-1 -5 -32 -544 ,*S-1 -5 -32 -551 SeShutdownPrivilege = *S-1 -5 -32 -544 ,*S-1 -5 -32 -545 ,*S-1 -5 -32 -551 SeTakeOwnershipPrivilege = *S-1 -5 -32 -544 SeDenyNetworkLogonRight = GuestSeDenyInteractiveLogonRight = GuestSeUndockPrivilege = *S-1 -5 -32 -544 ,*S-1 -5 -32 -545 SeManageVolumePrivilege = *S-1 -5 -32 -544 SeRemoteInteractiveLogonRight = *S-1 -5 -32 -544 ,*S-1 -5 -32 -555 SeImpersonatePrivilege = *S-1 -5 -19 ,*S-1 -5 -20 ,*S-1 -5 -32 -544 ,*S-1 -5 -6 SeCreateGlobalPrivilege = *S-1 -5 -19 ,*S-1 -5 -20 ,*S-1 -5 -32 -544 ,*S-1 -5 -6 SeIncreaseWorkingSetPrivilege = *S-1 -5 -32 -545 SeTimeZonePrivilege = *S-1 -5 -19 ,*S-1 -5 -32 -544 ,*S-1 -5 -32 -545 SeCreateSymbolicLinkPrivilege = *S-1 -5 -32 -544 SeDelegateSessionUserImpersonatePrivilege = *S-1 -5 -32 -544 [Version] signature ="$CHICAGO$" //校验非常重要Revision =1
描述:允许你用保存在数据库中的安全性设置来配置系统。1 2 3 4 secedit /configure /db filename [/cfg filename] [/overwrite][/areas area1 area2...] [/log filename] [/quiet] /overwrite - 指定在导入安全性模板前数据库应该被清空。如果没有指定此参数,在安全性模板中指定的将累积到数据库中。 /quiet - 指定配置操作的执行不需要提示用户进行任何确认。
基础示例:1 2 3 4 5 secedit /configure /cfg current.inf /overwrite /log hisecws.log secedit /configure /db model.sdb /cfg gp.inf /quiet 任务成功结束,有关详细信息,请参阅日志 %windir%\security\logs\scesrv.log。
secedit /import 可将安全性模板导入到数据库以便模板中指定的设置可应用到系统或作为分析系统的依据。1 secedit /import /db FileName .sdb /cfg FileName.inf [/overwrite] [/areasArea1 Area2 ...] [/logFileName] [/quiet]
基础示例:1 secedit /import /db hisecws.sdb /cfg hisecws.inf /overwrite
secedit /validate 描述:验证要导入到分析数据库或系统应用程序的安全模板的语法,在不同的系统下执行配置文件中的参数是不同的;1 2 3 4 语法: secedit /validate FileName /cfg filename - 指定要验证的安全模板。安全模板是用安全模板管理单元创 建的。
基础示例:1 2 3 secedit /validate /cfg current.ini 模版验证顺利完成,下列数据被忽略,数据无效。 SeDelegateSessionUserImpersonatePrivilege 不是有效特权。
secedit /analyze 可通过将其与数据库中的基本设置相比较,分析一台计算机上的安全设置。1 secedit /analyze /db FileName.sdb [/cfgFileName] [/overwrite] [/logFileName] [/quiet]
基础示例:1 secedit /analyze /db current.sdb /log result.txt
weiyigeek.top-
secedit /GenereateRollback 描述:可根据配置模板生成一个回滚模板。1 2 3 4 5 6 7 8 语法: secedit /generaterollback /cfg filename /rbk filename [/log filename] [/quiet] /db filename - 指定执行复原操作使用的数据库。 /cfg filename - 指定一个将要生成关于它的复原模板的安全模板。安全模板是用安全模板管理单元创建的。 /rbk filename - 指定一个复原信息要写入的安全模板。安全模板是用安全模板管理单元创建的。 示例:对于所有的文件名,如果没有指定路径,则是用当前目录。 secedit /generaterollback /db hisecws.sdb /cfg hisecws.inf /rbk hisecwsrollback.inf /log hisecws.log
附录脚本合规检查 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 if exist no.txt (del no.txt) cls echo 正在进行 "审计与帐户策略" 安全检查echo > list.txt PasswordComplexity = 1 echo >> list.txt MinimumPasswordLength = 8 echo >> list.txt MaximumPasswordAge = 42 echo >> list.txt MinimumPasswordAge = 1 echo >> list.txt PasswordHistorySize = 5 echo >> list.txt ClearTextPassword = 0 echo >> list.txt ResetLockoutCount = 15 echo >> list.txt LockoutDuration = 15 echo >> list.txt LockoutBadCount = 15 echo >> list.txt AuditPolicyChange = 3 echo >> list.txt AuditLogonEvents = 3 echo >> list.txt AuditObjectAccess = 3 echo >> list.txt AuditPrivilegeUse = 0 echo >> list.txt AuditProcessTracking = 0 echo >> list.txt AuditDSAccess = 0 echo >> list.txt AuditSystemEvents = 3 echo >> list.txt AuditAccountLogon = 3 echo >> list.txt AuditAccountManage = 3 secedit /export /cfg model.inf >nul for /F "tokens=1 ,3 " %%i in (list.txt) do (call :Getgp %%i %%j ) ping 127 .0 .0 .1 /n 2 >nul del tmp.txtdel list.txtdel model.infgoto :EOF:Getgp find "%1 " model.inf >tmp.txtfor /f "skip=2 tokens=3 " %%i in (tmp.txt) do (if "%%i "=="%2 " (echo %1=% %i ok) else (echo %1 策略不符合规则>>bad.txt)) goto :EOF