[TOC]
0x00 前言导读 Q: 什么是 Web UI (Dashboard) ?
答: Kubernetes Dashboard 是一个通用的、基于web的Kubernetes集群UI。它允许用户管理在集群中运行的应用程序并对它们进行故障排除,以及管理集群本身。
Q: 为什么要使用 Dashboard?
答: 您可以使用 Dashboard 来概述集群上运行的应用程序,以及创建或修改单个Kubernetes资源(例如Deployments,Jobs,DaemonSets等)例如,您可以使用部署向导来扩展部署,启动滚动更新,重新启动Pod或部署新应用程序。
附录: https://kubernetes.io/docs/tasks/access-application-cluster/web-ui-dashboard/ https://github.com/kubernetes/dashboard
0x01 安装部署 (1) 环境准备 Kubernetes 环境: 集群环境实现业务高可用以及快速扩容缩
[TOC]
0x00 前言导读 Q: 什么是 Web UI (Dashboard) ?
答: Kubernetes Dashboard 是一个通用的、基于web的Kubernetes集群UI。它允许用户管理在集群中运行的应用程序并对它们进行故障排除,以及管理集群本身。
Q: 为什么要使用 Dashboard?
答: 您可以使用 Dashboard 来概述集群上运行的应用程序,以及创建或修改单个Kubernetes资源(例如Deployments,Jobs,DaemonSets等)例如,您可以使用部署向导来扩展部署,启动滚动更新,重新启动Pod或部署新应用程序。
附录: https://kubernetes.io/docs/tasks/access-application-cluster/web-ui-dashboard/ https://github.com/kubernetes/dashboard
0x01 安装部署 (1) 环境准备 Kubernetes 环境: 集群环境实现业务高可用以及快速扩容缩 1 2 3 4 5 6 7 8 9 ~$ kubectl get nodes NAME STATUS ROLES AGE VERSION weiyigeek-107 Ready master 25h v1.19.6 weiyigeek-108 Ready master 25h v1.19.6 weiyigeek-109 Ready master 25h v1.19.6 weiyigeek-223 Ready <none> 17h v1.19.6 weiyigeek-224 Ready <none> 17h v1.19.6 weiyigeek-225 Ready <none> 17h v1.19.6 weiyigeek-226 Ready <none> 17h v1.19.6
(2) 安装流程 描述: 我们可以通过原生的dashboardyaml资源清单文件或者helm的方式进行安装
官方 安装方式 安装参考: https://github.com/kubernetes/dashboard/blob/master/docs/user/installation.md
1 2 3 4 5 6 7 8 9 10 11 12 13 14 kubectl create secret generic kubernetes-dashboard-certs --from-file=$HOME /certs -n kubernetes-dashboard kubectl create --edit -f https://raw.githubusercontent.com/kubernetes/dashboard/v2.1.0/aio/deploy/recommended.yaml containers: - args: - --tls-cert-file=/tls.crt - --tls-key-file=/tls.key
Step 3.仪表板仅通过HTTP公开不使用证书方式部署(不推荐)1 kubectl create -f https://raw.githubusercontent.com/kubernetes/dashboard/v2.0.1/aio/deploy/alternative.yaml
weiyigeek.top-Kubernetes Dashboard
参考地址: https://github.com/kubernetes/dashboard/blob/master/README.md
Helm 安装方式 操作流程: 此处对于helm安装不再累述,二进制安装没有什么好说的;1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 $ helm repo add k8s-dashboard https://kubernetes.github.io/dashboard $ helm pull k8s-dashboard/kubernetes-dashboard --untar ~/K8s/Day10/dashboard$ tar -xzvf kubernetes-dashboard-3.0.0.tgz ~/K8s/Day10/dashboard$ ls kubernetes-dashboard ~/K8s/Day10/dashboard$ helm install kubernetes-dashboard kubernetes-dashboard/ --namespace kube-system
查看结果:1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 ~/K8s/Day10/dashboard$ helm list -n kube-system ~/K8s/Day10/dashboard$ helm history kubernetes-dashboard -n kube-system ~/K8s/Day10/dashboard$ kubectl get pod -n kube-system -o wide --show-labels | grep "kubernetes-dashboard-879457794-kxvcr" ~/K8s/Day10/dashboard$ kubectl get svc -n kube-system -o wide | grep "kubernetes-dashboard"
以NodePort的方式进行访问:1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 ~/K8s/Day10/dashboard$ kubectl edit svc -n kube-system kubernetes-dashboard service/kubernetes-dashboard edited apiVersion: v1 kind: Service metadata: annotations: meta.helm.sh/release-name: kubernetes-dashboard meta.helm.sh/release-namespace: kube-system creationTimestamp: "2020-12-06T13:45:22Z" labels: app.kubernetes.io/component: kubernetes-dashboard app.kubernetes.io/instance: kubernetes-dashboard app.kubernetes.io/managed-by: Helm app.kubernetes.io/name: kubernetes-dashboard app.kubernetes.io/version: 2.0 .4 helm.sh/chart: kubernetes-dashboard-3.0.0 kubernetes.io/cluster-service: "true" name: kubernetes-dashboard namespace: kube-system resourceVersion: "6111082" selfLink: /api/v1/namespaces/kube-system/services/kubernetes-dashboard uid: 51025 b69-7c65-4ac0-a8f2-93a243a33e7d spec: clusterIP: 10.104 .18 .192 ports: - name: https port: 443 protocol: TCP targetPort: https nodePort: 30443 selector: app.kubernetes.io/component: kubernetes-dashboard app.kubernetes.io/instance: kubernetes-dashboard app.kubernetes.io/name: kubernetes-dashboard sessionAffinity: None type: NodePort status: loadBalancer: {}
简单使用:
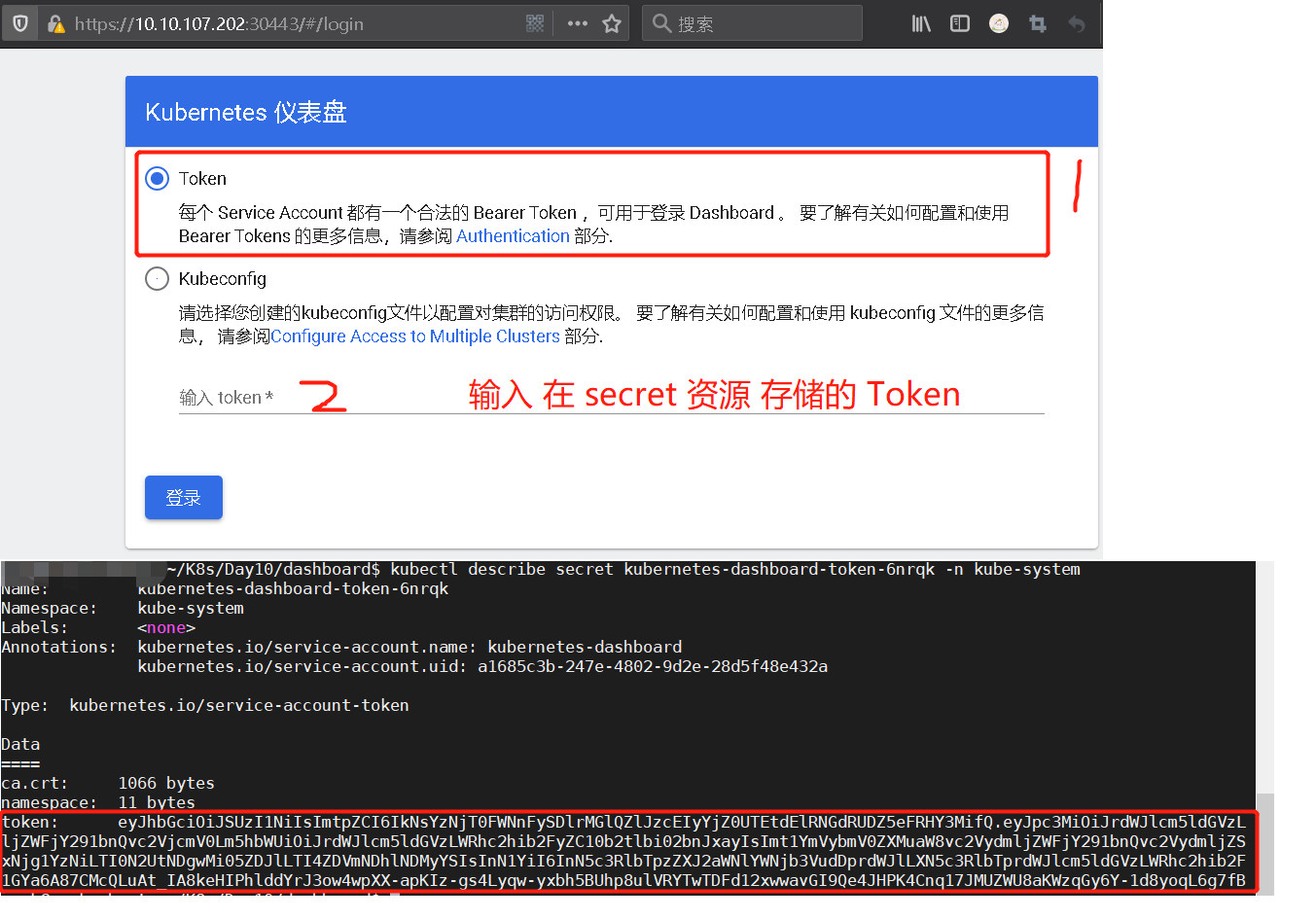
1) 认证的 Token 查看1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 ~/K8s/Day10/dashboard$ kubectl -n kube-system get secret | grep kubernetes-dashboard-token kubectl describe secret kubernetes-dashboard-token-6nrqk -n kube-system
weiyigeek.top-Kubernetes-仪表盘
PS : 需要注意令牌过期时间,登录账户将自动退出;
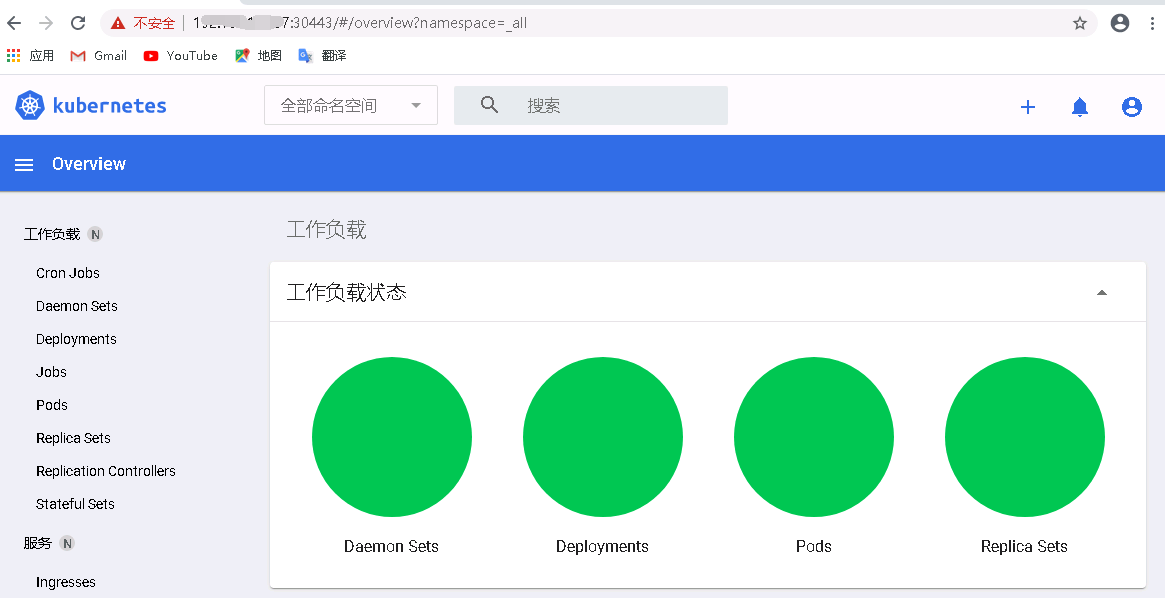
2) 登录Dashboard仪表盘控制台,可以看相关资源控制器下面的所属资源
weiyigeek.top-Dashboard仪表盘主页
参考地址:https://artifacthub.io/packages/helm/k8s-dashboard/kubernetes-dashboard?modal=install
安装部署 v2.5.1 版本 描述: 当前时间节点【2022年5月13日 16:50:07】,相对比于前面的 kubernetes-dashboard 版本,当前安装可能会有一定差异。
步骤 01.从Github中拉取dashboard部署资源清单,当前最新版本v2.5.11 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 wget -L https://raw.githubusercontent.com/kubernetes/dashboard/v2.5.1/aio/deploy/recommended.yaml kubectl apply -f recommended.yaml grep "image:" recommended.yaml kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/v2.5.1/aio/deploy/recommended.yaml
步骤 02.查看部署的dashboard相关资源是否正常。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 $ kubectl get deploy,svc -n kubernetes-dashboard -o wide NAME READY UP-TO-DATE AVAILABLE AGE CONTAINERS IMAGES SELECTOR deployment.apps/dashboard-metrics-scraper 1/1 1 1 7m45s dashboard-metrics-scraper kubernetesui/metrics-scraper:v1.0.7 k8s-app=dashboard-metrics-scraper deployment.apps/kubernetes-dashboard 1/1 1 1 7m45s kubernetes-dashboard kubernetesui/dashboard:v2.5.1 k8s-app=kubernetes-dashboard NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE SELECTOR service/dashboard-metrics-scraper ClusterIP 10.96.37.134 <none> 8000/TCP 7m45s k8s-app=dashboard-metrics-scraper service/kubernetes-dashboard ClusterIP 10.96.26.57 <none> 443/TCP 7m45s k8s-app=kubernetes-dashboard $ kubectl edit svc -n kubernetes-dashboard kubernetes-dashboard apiVersion: v1 kind: Service ..... spec: ..... ports: - port: 443 protocol: TCP targetPort: 8443 nodePort: 30443 selector: k8s-app: kubernetes-dashboard sessionAffinity: None type : NodePort
步骤 03.默认仪表板部署包含运行所需的最小RBAC权限集,而要想使用dashboard操作集群中的资源,通常我们还需要自定义创建kubernetes-dashboard管理员角色。https://github.com/kubernetes/dashboard/blob/master/docs/user/access-control/README.md
1 2 3 kubectl get sa -n kubernetes-dashboard kubernetes-dashboard kubectl describe secrets -n kubernetes-dashboard kubernetes-dashboard-token-jhdpb | grep '^token:' |awk '{print $2}'
weiyigeek.top-Dashboard默认两种认证方式
Kubernetes Dashboard 支持几种不同的用户身份验证方式:
Authorization header
Bearer Token (默认)
Username/password
Kubeconfig file (默认)
温馨提示: 此处使用Bearer Token方式, 为了方便演示我们向 Dashboard 的服务帐户授予管理员权限 (Admin privileges), 而在生产环境中通常不建议如此操作, 而是指定一个或者多个名称空间下的资源进行操作。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 tee rbac-dashboard-admin.yaml <<'EOF' apiVersion: v1 kind: ServiceAccount metadata: name: dashboard-admin namespace: kubernetes-dashboard --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: dashboard-admin namespace: kubernetes-dashboard roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: cluster-admin subjects: - kind: ServiceAccount name: dashboard-admin namespace: kubernetes-dashboard EOF kubectl apply -f rbac-dashboard-admin.yaml
步骤 04.获取 sa 创建的 dashboard-admin 用户的 secrets 名称并获取认证 token ,用于上述搭建的dashboard 认证使用。1 2 3 4 5 kubectl get sa -n kubernetes-dashboard dashboard-admin -o yaml | grep "\- name" | awk '{print $3}' kubectl describe secrets -n kubernetes-dashboard dashboard-admin-token-crh7v | grep "^token:" | awk '{print $2}' eyJhbGciOiJSUzI1NiIsImtpZCI6IkJXdm1YSGNSQ3VFSEU3V0FTRlJKcU10bWxzUDZPY3lfU0lJOGJjNGgzRXMifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4tY3JoN3YiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiNDY3ODEwMDMtM2MzNi00NWE1LTliYTQtNDY3MTQ0OWE2N2E0Iiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmVybmV0ZXMtZGFzaGJvYXJkOmRhc2hib2FyZC1hZG1pbiJ9.X10AzWBxaHObYGoOqjfw3IYkhn8L5E7najdGSeLavb94LX5BY8_rCGizkWgNgNyvUe39NRP8r8YBU5sy9F2K-kN9_5cxUX125cj1drLDmgPJ-L-1m9-fs-luKnkDLRE5ENS_dgv7xsFfhtN7s9prgdqLw8dIrhshHVwflM_VOXW5D26QR6izy2AgPNGz9cRh6x2znrD-dpUNHO1enzvGzlWj7YhaOUFl310V93hh6EEc57gAwmDQM4nWP44KiaAiaW1cnC38Xs9CbWYxjsfxd3lObWShOd3knFk5PUVSBHo0opEv3HQ_-gwu6NGV6pLMY52p_JO1ECPSDnblVbVtPQ
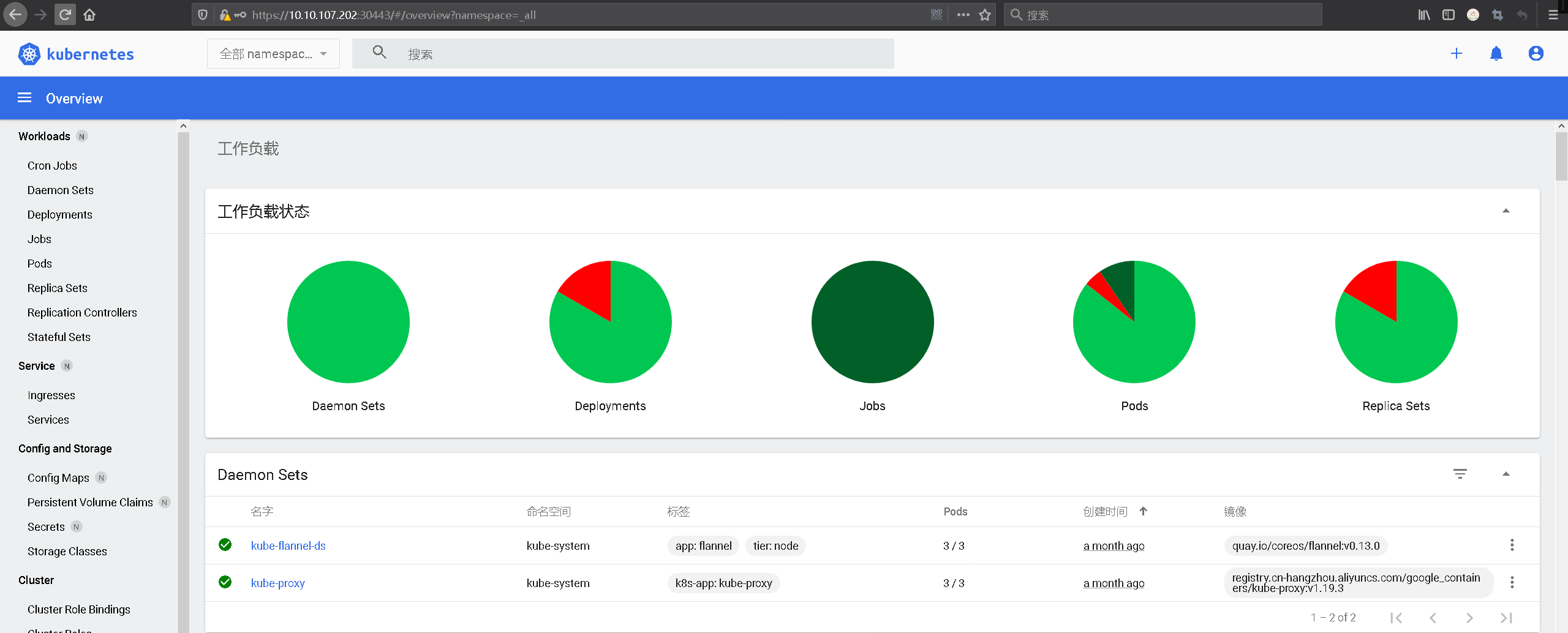
步骤 05.利用上述 Token 进行登陆Kubernetes-dashboard的UI。
weiyigeek.top-拥有管理员权限的dashboard
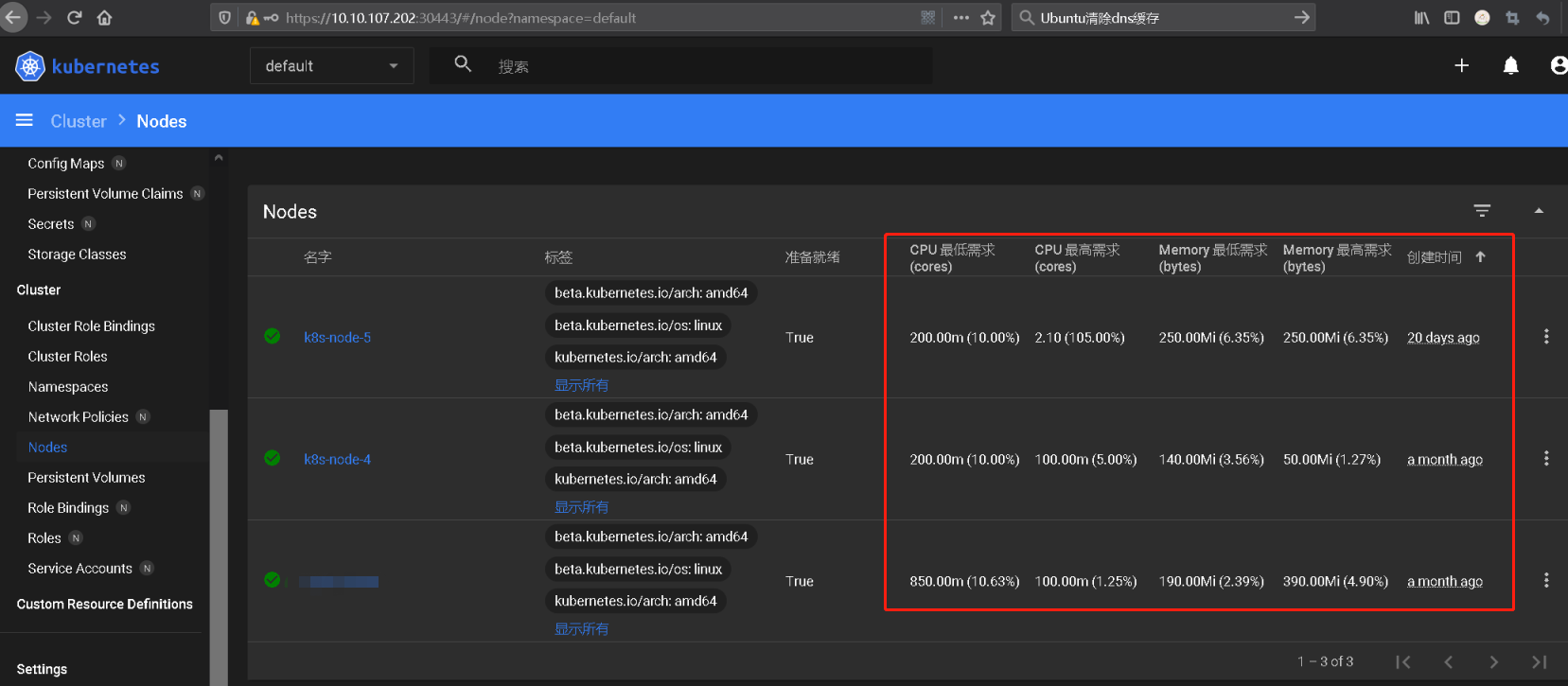
(3) MetricServer Q: MetricServer 是什么?
答: 它是kubernetes集群资源使用情况的聚合器,收集数据给kubernetes集群内使用,如 kubectl,hpa,scheduler等。
PS : 如果采用官方的安装dashboard的方式则默认将Metric Server进行安装使用,而采用helm安装dashboard时候默认是将metrics-server禁用的需要手动启用;
helm 安装方式 下面我们使用Helm部署Dashboard时也可以利用第三方依赖进行安装metrics-server,只需要修改一个小小的注释1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 $ ~/K8s/Day10/dashboard/kubernetes-dashboard$ vim +200 values.yaml metrics-server: enabled: true args: - --logtostderr - --kubelet-preferred-address-types=InternalIP - --kubelet-insecure-tls ~/K8s/Day10/dashboard$ kubectl edit svc -n kube-system kubernetes-dashboard service/kubernetes-dashboard edited ~/K8s/Day10/dashboard$ helm upgrade kubernetes-dashboard kubernetes-dashboard/ -n kube-system ~/K8s/Day10/dashboard$ kubectl get pod -n kube-system -o wide | grep "kubernetes-dashboard" ~/K8s/Day10/dashboard$ kubectl describe pod kubernetes-dashboard-metrics-server-7bc85c65bc-vrxft -n kube-system kubernetes-dashboard Warning Failed 10m (x4 over 12m) kubelet Failed to pull image "k8s.gcr.io/metrics-server-amd64:v0.3.6" : rpc error: code = Unknown desc = Error response from daemon: Get https://k8s.gcr.io/v2/: net/http: request canceled while waiting for connection (Client.Timeout exceeded while awaiting headers) ~/K8s/Day10/dashboard$ docker pull registry.cn-hangzhou.aliyuncs.com/google_containers/metrics-server-amd64:v0.3.6 ~/K8s/Day10/dashboard$ docker tag registry.cn-hangzhou.aliyuncs.com/google_containers/metrics-server-amd64:v0.3.6 k8s.gcr.io/metrics-server-amd64:v0.3.6 ~/K8s/Day10/dashboard$ docker save k8s.gcr.io/metrics-server-amd64:v0.3.6 -o metrics-server-amd64.tar ~/K8s/Day10/dashboard$ scp -P 20211 metrics-server-amd64.tar weiyigeek@10.10.107.215:~ ~/K8s/Day10/dashboard$ ssh -p 20211 weiyigeek@10.10.107.215 "docker load -i metrics-server-amd64.tar" ~/K8s/Day10/dashboard$ kubectl get pod -n kube-system -o wide | grep "kubernetes-dashboard-metrics-server-7bc85c65bc-vrxft" ~$ kubectl top pod ~$ kubectl top node export POD_NAME=$(kubectl get pods -n kube-system -l "app.kubernetes.io/name=kubernetes-dashboard,app.kubernetes.io/instance=kubernetes-dashboard" -o jsonpath="{.items[0].metadata.name}" )echo https://127.0.0.1:30443/~/K8s/Day10/dashboard$ kubectl -n kube-system port-forward --address 10.10.107.202 $POD_NAME 30443:8443 ~/K8s/Day10/dashboard$ kubectl describe secrets -n kube-system kubernetes-dashboard-token-6nrqk token: eyJhbGciOiJSUzI1Ni................IsImtpZCI6IkNsknTWtKLBDUk-Q ~$ helm get all -n kube-system kubernetes-dashboard ~$ helm uninstall kubernetes-dashboard -n kube-system release "kubernetes-dashboard" uninstalled
weiyigeek.top-K8s-metrics-server
(4) 配置扩展 1.配置 Kubernetes-dashboard 以支持 http 方式访问 描述: 当前默认安装配置的 Kubernetes-dashboard 都是启用了https, 然而在当我们环境中存在ingress时,可能会有需要将其通过虚拟主机进行暴露时,此时将会在ingress端进行设置证书而不是在 Kubernetes-dashboard Pod中设置证书。
步骤 01.打开下载的Kubernetes-dashboard资源清单文件或者使用kubelet edit命令编辑已部署的资源清单,首先配置 kubernetesui/dashboard:v2.5.1 镜像的启动参数,主要是--enable-insecure-login与--insecure-port=8080参数。1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 $ kubectl edit deployments.apps -n kubernetes-dashboard kubernetes-dashboard args: - --namespace=kubernetes-dashboard - --enable -insecure-login - --insecure-port=8080 ports: - name: https containerPort: 8443 protocol: TCP - name: http containerPort: 8080 protocol: TCP livenessProbe: httpGet: scheme: HTTP path: / port: 8080
步骤 02.配置 kubernetes-dashboard 的 Service 资源管理器
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 $ kubectl edit svc -n kubernetes-dashboard kubernetes-dashboard ports: - name: https port: 443 protocol: TCP targetPort: 8443 - name: http port: 8080 protocol: TCP targetPort: 8080 selector: k8s-app: kubernetes-dashboard sessionAffinity: None type : ClusterIP $ kubectl get svc -n kubernetes-dashboard kubernetes-dashboard NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE kubernetes-dashboard ClusterIP 11.19.103.247 <none> 443/TCP,8080/TCP 3h39m
步骤 03.服务验证以及部署ingress转发规则URL设置,最后浏览器访问如下URL(devops.weiyigeek.top/dashboard/)即可。1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 $ curl 11.19.103.247:8080 $ tee kubernetes-dashboard-ingress.yaml <<'EOF' apiVersion: networking.k8s.io/v1 kind: Ingress metadata: annotations: ingressclass.kubernetes.io/is-default-class: "true" nginx.ingress.kubernetes.io/proxy-connect-timeout: "75" nginx.ingress.kubernetes.io/proxy-read-timeout: "300" nginx.ingress.kubernetes.io/proxy-send-timeout: "300" nginx.ingress.kubernetes.io/rewrite-target: /$2 labels: app: devops-weiyigeek name: devops-weiyigeek namespace: kubernetes-dashboard spec: ingressClassName: nginx rules: - host: devops.weiyigeek.top http: paths: - backend: service: name: kubernetes-dashboard port: number: 8080 path: /dashboard(/|$)(.*) pathType: ImplementationSpecific tls: - hosts: - devops.weiyigeek.top secretName: devops-weiyigeek-top EOF $ kubectl apply -f kubernetes-dashboard-ingress.yaml $ kubectl get ingress -n kubernetes-dashboard devops-weiyigeek NAME CLASS HOSTS ADDRESS PORTS AGE devops-weiyigeek nginx devops.weiyigeek.top 11.19.12.210 80, 443 3h52m
温馨提示: 在前面部署完成后, 我们便可可以通过https://devops.weiyigeek.top/dashboard/带https + 域名方式访问kubernetes-dashboard了。
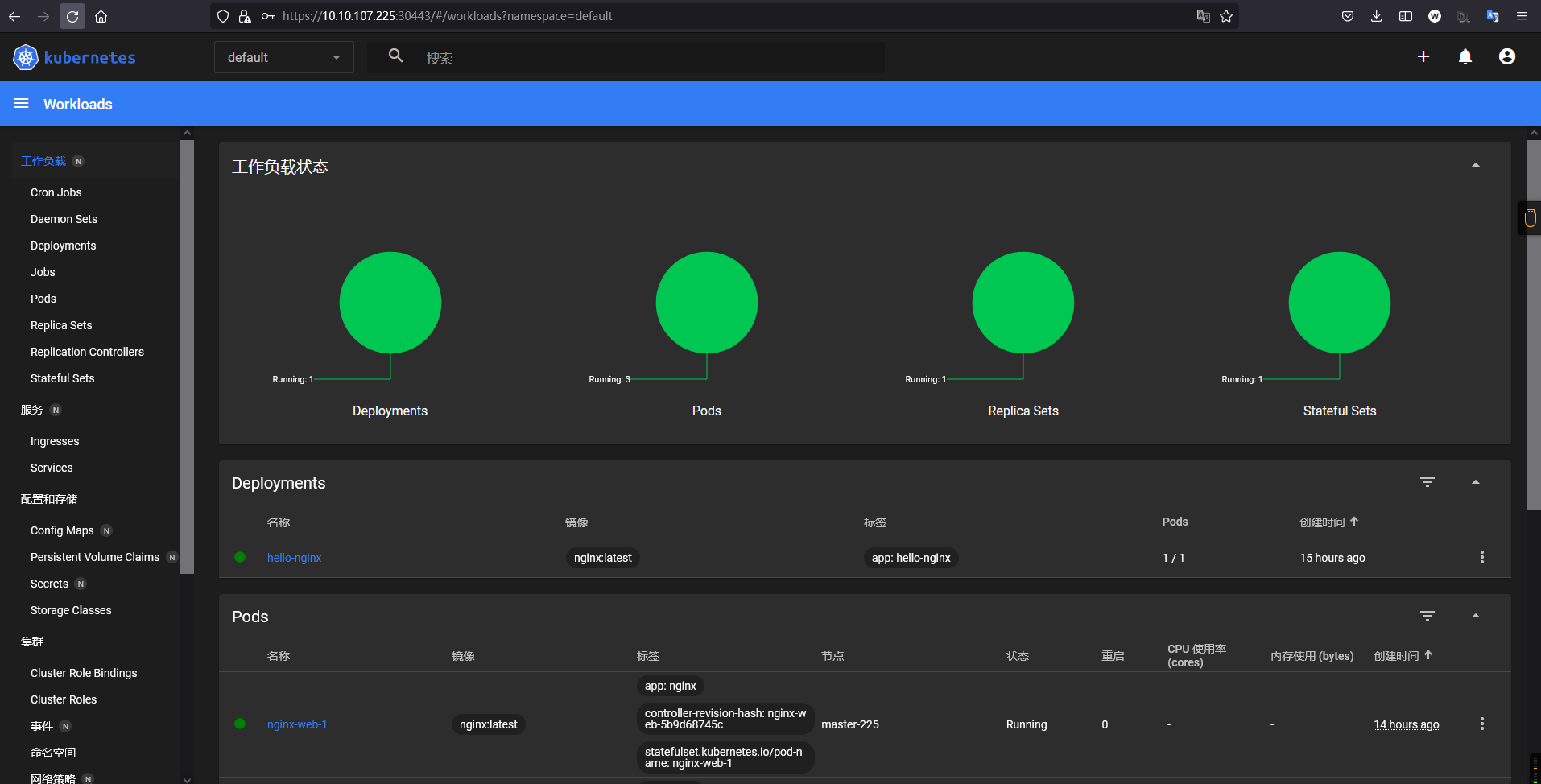
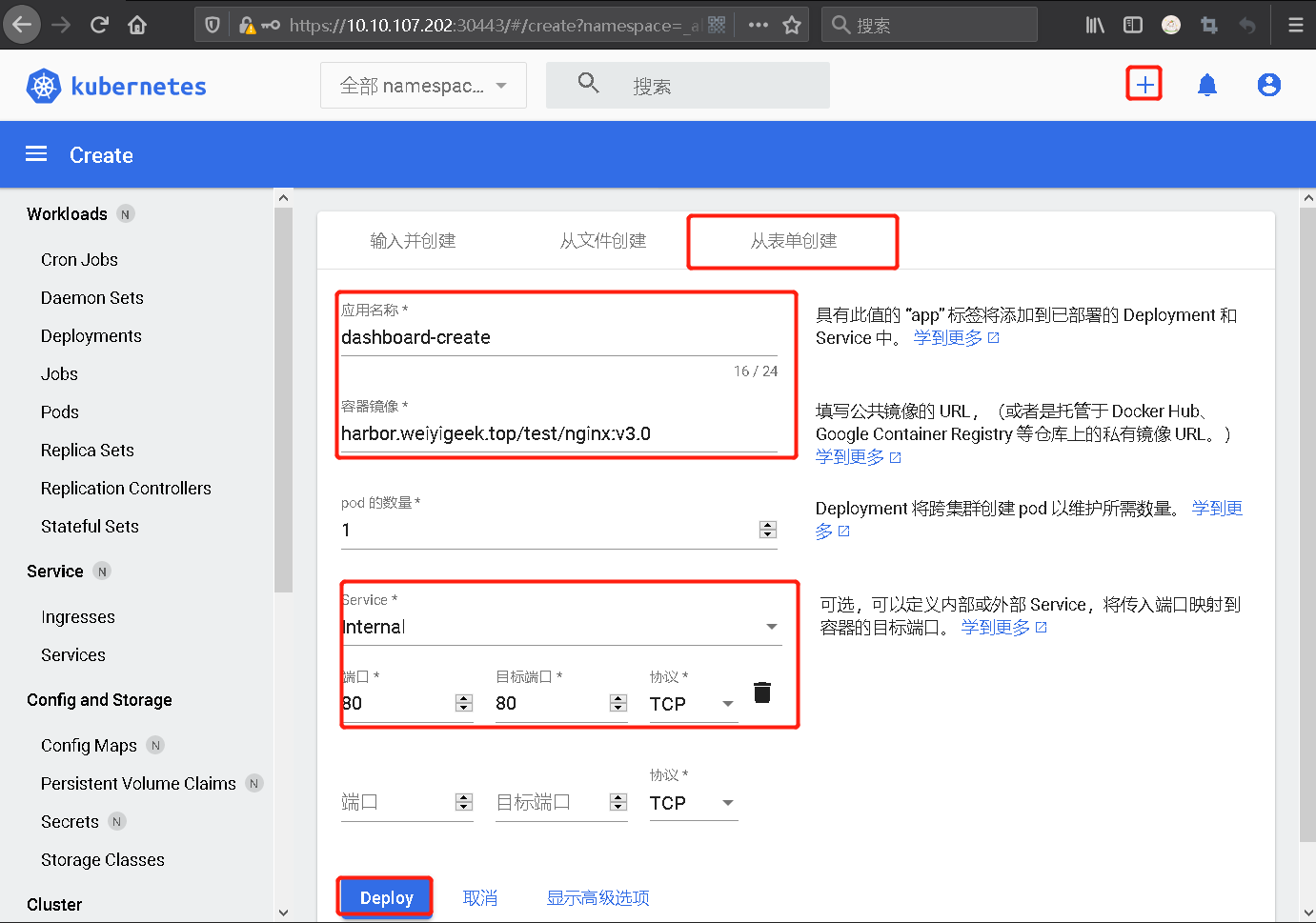
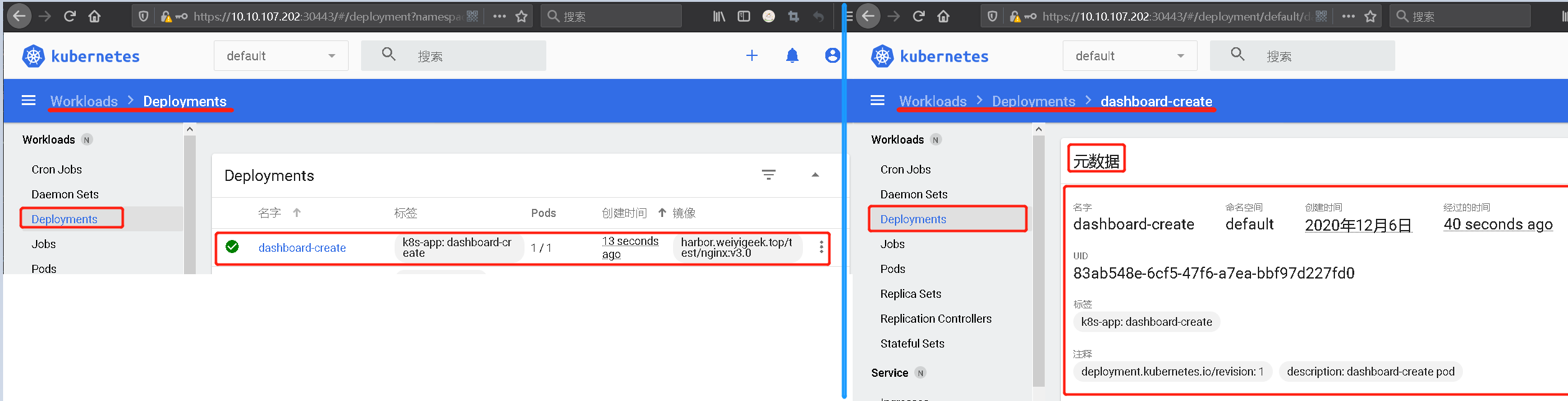
0x03 使用实践 (1) Dashboard-小试牛刀之简单初识
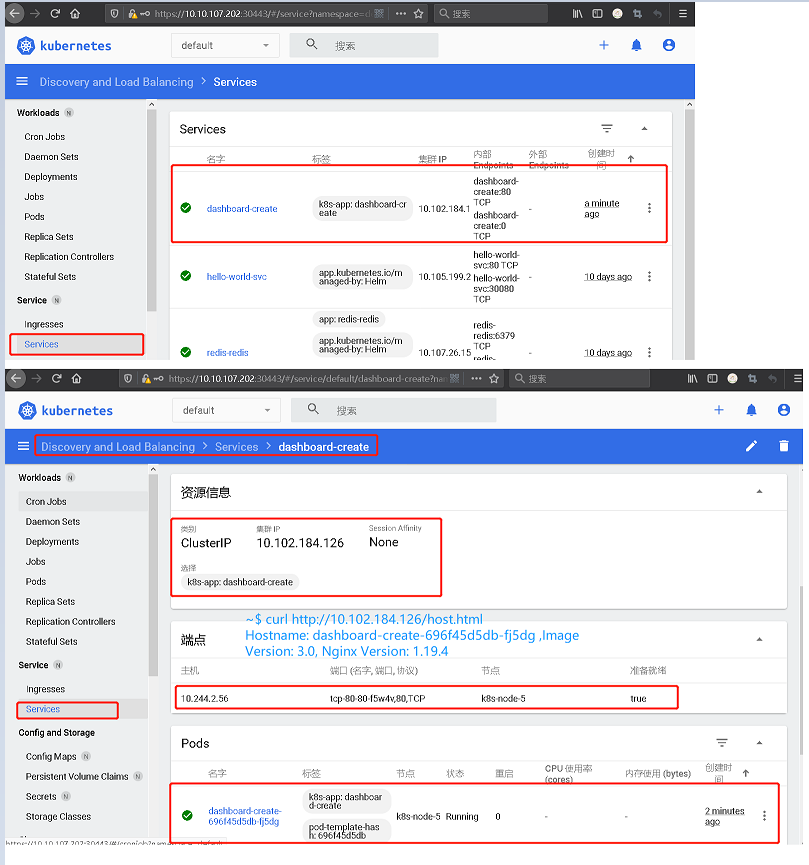
Step 1.右上角点击+进行创建Deployment管理的Pod,按图所示输入应用名称和容器镜像名称,其次是Services资源控制器设置为内部的Internal;
weiyigeek.top-创建Deployment管理的Pod
weiyigeek.top-Service
Step 4.#验证 集群IP地址访问 以及 Pod地址访问效果一致1 2 3 ~$ curl http://10.102.184.126/host.html && curl http://10.244.2.56/host.html
PS : 总结可以看出使用Kubernetes-Kuboard是可以非常简单的创建我们指定的应用到kubernetes之中;
(2) Dashboard-利用rbac机制限制指定用户针对指定名称空间中的资源进行UI管理。 描述: 有时可能我们会遇到如下场景, 在进行持续CI/CD后,开发人员可能会需要查看部署应用的启动日志,如果都是我们运维人员手动去截图发给他们, 那这样的效率简直是在浪费生命,所有为了节约时间同时保证防止开发人员误操作集群, 此时我们只赋予其指定名称空间下的某些资源浏览权限即可.
在 Kubernetes 集群中我们可以使用 rbac 授权机制, 做用户角色权限分离,可以指定那些资源,我们可以进行那些操作,然后把该角色赋予给指定的用户,最好利用该用户的Token进行登陆Kubernetes-Dashborad界面进行相应管理。
步骤 01.创建一个服务用户此处我们可以采用两种方式创建资源清单或者命令行。1 2 3 4 5 6 7 8 9 10 11 kubectl create serviceaccount -n devtest devtest-ns-viewonly tee > devtest-ns-viewonly-sa.yaml <<'EOF' apiVersion: v1 kind: ServiceAccount metadata: name: devtest-ns-viewonly namespace: devtest EOF
步骤 02.准备名称为dashboard-viewonly角色相关资源权限操作的资源清单。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 tee > dashboard-namespace-viewonly.yaml <<'EOF' kind: Role apiVersion: rbac.authorization.k8s.io/v1 metadata: name: dashboard-viewonly namespace: devtest rules: - apiGroups: ["" ] resources: ["pods" ,"pods/exec" ] verbs: ["get" ,"list" ,"watch" ,"delete" ] - apiGroups: - "" resources: - configmaps - endpoints - persistentvolumeclaims - persistentvolumeclaims/status - replicationcontrollers - replicationcontrollers/scale - serviceaccounts - services - services/status verbs: - get - list - watch - apiGroups: - "" resources: - bindings - events - limitranges - namespaces/status - pods/log - pods/status - replicationcontrollers/status - resourcequotas - resourcequotas/status verbs: - get - list - watch - apiGroups: - "" resources: - namespaces verbs: - get - list - watch - apiGroups: - apps resources: - controllerrevisions - daemonsets - daemonsets/status - deployments - deployments/scale - deployments/status - replicasets - replicasets/scale - replicasets/status - statefulsets - statefulsets/scale - statefulsets/status verbs: - get - list - watch - apiGroups: - extensions resources: - daemonsets - daemonsets/status - deployments - deployments/scale - deployments/status - ingresses - ingresses/status - networkpolicies - replicasets - replicasets/scale - replicasets/status - replicationcontrollers/scale verbs: - get - list - watch - apiGroups: - batch resources: - cronjobs - cronjobs/status - jobs - jobs /status verbs: - get - list - watch - apiGroups: - networking.k8s.io resources: - ingresses - ingresses/status - networkpolicies verbs: - get - list - watch - apiGroups: - metrics.k8s.io resources: - pods - nodes verbs: - get - list - watch EOF kubectl apply -f dashboard-namespace-viewonly.yaml
步骤 03.绑定 dashboard-viewonly 角色给 ServiceAccount 的 devtest-ns-viewonly 用户.1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 tee dashboard-viewonly-RoleBinding<<'EOF' kind: RoleBinding apiVersion: rbac.authorization.k8s.io/v1 metadata: name: devtest-ns-viewonly namespace: devtest roleRef: kind: Role name: dashboard-viewonly apiGroup: rbac.authorization.k8s.io subjects: - kind: ServiceAccount name: devtest-ns-viewonly EOF kubectl create rolebinding -n devtest devtest-ns-viewonly --role=devtest:dashboard-viewonly --serviceaccount=devtest-ns-viewonly
温馨提示: ClusterRole 与 ClusterRoleBinding 均不支持指定名称空间。
步骤 04.查看 devtest-ns-viewonly 用户存在 secrets 中的认证Token。1 kubectl describe secrets -n devtest devtest-ns-viewonly-token-gxgps | grep "^token:" | awk '{print $2}'
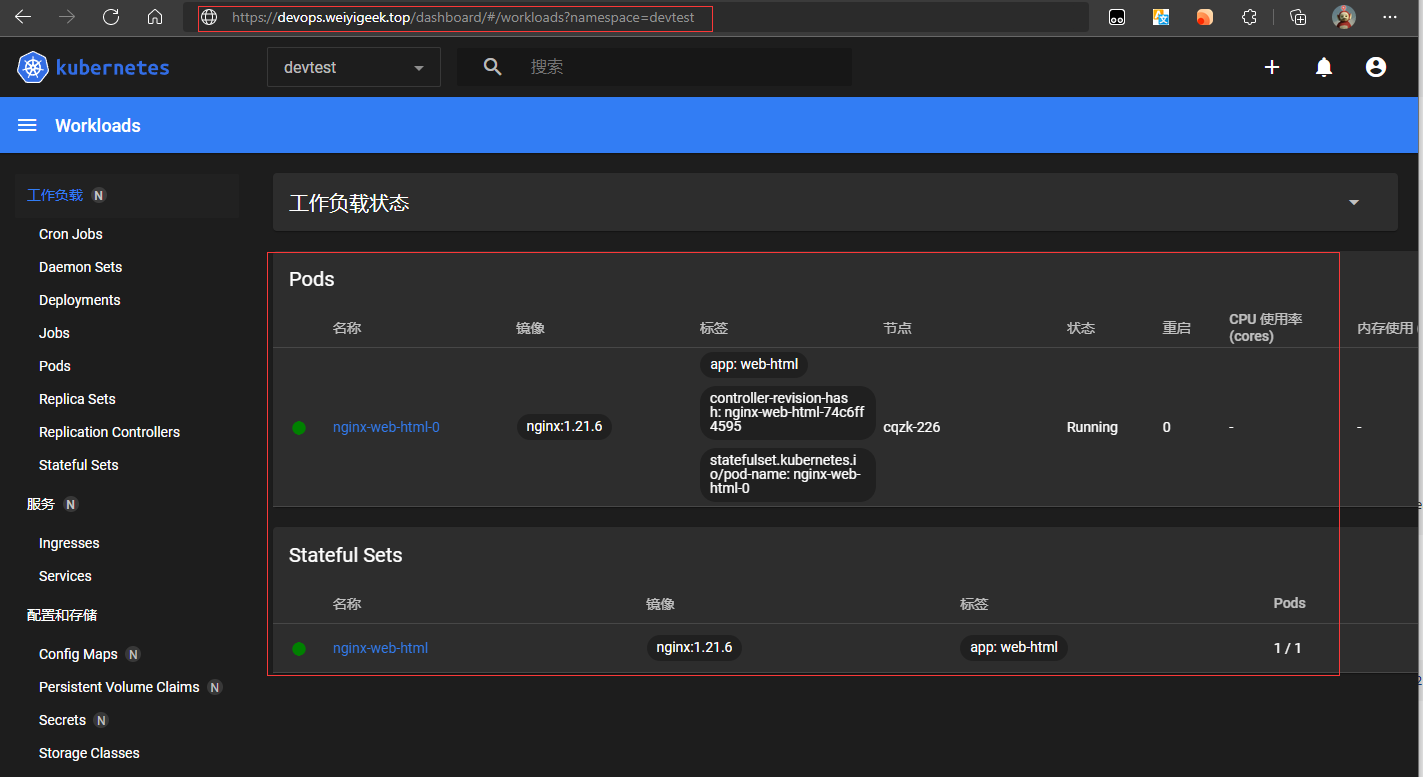
步骤 05.使用获取到的Token访问登陆,我们搭建的kubernetes-dashboard Web UI,此处使用浏览器访问(https://devops.weiyigeek.top/dashboard/#/workloads?namespace=devtest),可以看到该使用Token认证的用户只能访问devtest名称空间下的特定资源。
weiyigeek.top-认证用户只能访问devtest名称空间下的特定资源
0x04 入坑与出坑 问题1.pods is forbidden: User "system:serviceaccount:kube-system:namespace-controller" cannot create resource clusterroles” in API group “rbac.authorization.k8s.io” at the cluster scope 问题原因:
1.API组中用户不能在默认命名空间创建Pod,也就是说使用原token认证登录的用户是无权操作
2.其次是采用Helm创建的时候只是将kubernetes-dashboard-metrics与集群角色绑定1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 ~/K8s/Day10/dashboard/kubernetes-dashboard$ kubectl get ClusterRoleBinding -n kube-system | grep "kubernetes-dashboard" kubernetes-dashboard-metrics ClusterRole/kubernetes-dashboard-metrics ~/K8s/Day10/dashboard/kubernetes-dashboard$ kubectl get clusterrole ~/K8s/Day10/dashboard/kubernetes-dashboard$ kubectl get clusterrole kubernetes-dashboard-metrics -o yaml rules: - apiGroups: - metrics.k8s.io resources: - pods - nodes verbs: - get - list - watch
解决方法:1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 cat > k8s-admin.yaml <<'EOF' apiVersion: v1 kind: ServiceAccount metadata: name: kubernetes-dashboard namespace: kube-system --- kind: ClusterRoleBinding apiVersion: rbac.authorization.k8s.io/v1 metadata: name: kubernetes-dashboard subjects: - kind: ServiceAccount name: kubernetes-dashboard namespace: kube-system roleRef: kind: ClusterRole name: cluster-admin apiGroup: rbac.authorization.k8s.io EOF kubectl create -f k8s-admin.yaml ~/K8s/Day10/dashboard/$ kubectl get ClusterRoleBinding -n kube-system | grep "kubernetes-dashboard" ~/K8s/Day10/dashboard/$ kubectl describe ClusterRoleBinding -n kube-system kubernetes-dashboard kubectl describe secret kubernetes-dashboard-token-7z6zm -n kube-system
PS : 在使用Helm创建Kubenertes-Dashboard时候已创建了ServiceAccount资源,所以只需要创建ClusterRoleBinding资源即可;
参考地址: https://blog.csdn.net/qq_38900565/article/details/100729686
问题2.采用Helm安装metric-server时镜像有误导致Pod状态ImagePullBackOff 错误信息:1 Warning Failed 10m (x4 over 12m) kubelet Failed to pull image "k8s.gcr.io/metrics-server-amd64:v0.3.6" : rpc error: code = Unknown desc = Error response from daemon: Get https://k8s.gcr.io/v2/: net/http: request canceled while waiting for connection (Client.Timeout exceeded while awaiting headers)
1.利用阿里云的K8s镜像站拉取metrics-server-amd64:v0.3.6镜像然后进行改名,随后上传到metrics-server运行的节点之上
2.在进行更新时候指定或者说修改配置文件中的image.repository;1 2 3 ~/K8s/Day10/dashboard$ grep "k8s.gcr.io" kubernetes-dashboard/charts/metrics-server/* ~/K8s/Day10/dashboard$ sed -i "s#k8s.gcr.io#registry.cn-hangzhou.aliyuncs.com/google_containers#g" kubernetes-dashboard/charts/metrics-server/values.yaml: